How to configure Jazz Authentication Server with App ID on IBM Cloud
Authors: -- TadahiroHara - 2020-11-26Build basis: ELM 7.0.2 and higher
Starting with the Collaborative Lifecycle Management Solution 6.0 software release, Jazz Security Architecture SSO is available as an authentication option. Based on OpenID Connect , authentication is NOT performed by the container hosting Jazz applications, but instead is delegated to a separate Jazz Authorization Server (JAS), which performs the role of an OpenID Connect provider (OP).
For further Information on Jazz Security Architecture you can visit our jazz.net article Jazz Server Authentication Explained
You can configure the Liberty OpenID Connect Provider to further delegate the user authentication like App ID on IBM cloud using the Liberty "Social Login" feature.
This article shows an example of configuration with JAS and App ID.
The configuration information are extracted and modified for JAS from Liberty Topic: Configuring Social Login in Liberty and Configuring CLM Authentication with a 3rd Party OIDC provider
 Adding an application in App ID.
Adding an application in App ID.
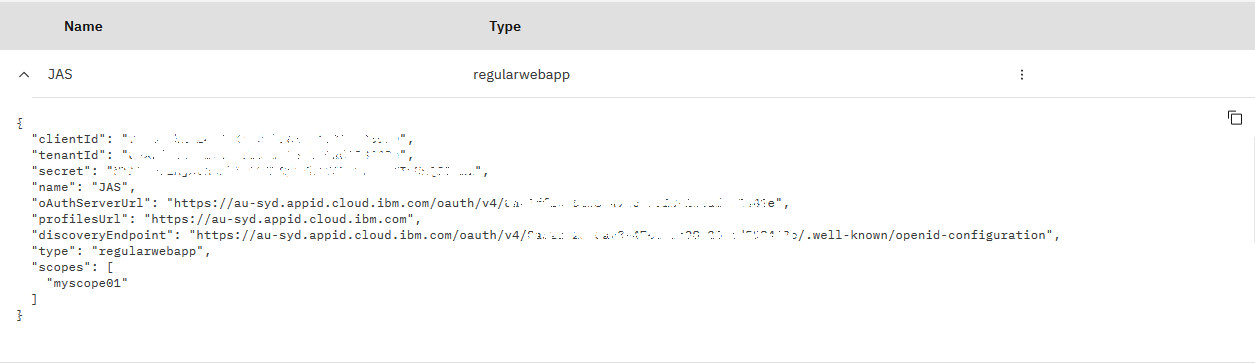
 You can get information for liberty OIDC settings after adding an "Application".
You can get information for liberty OIDC settings after adding an "Application".
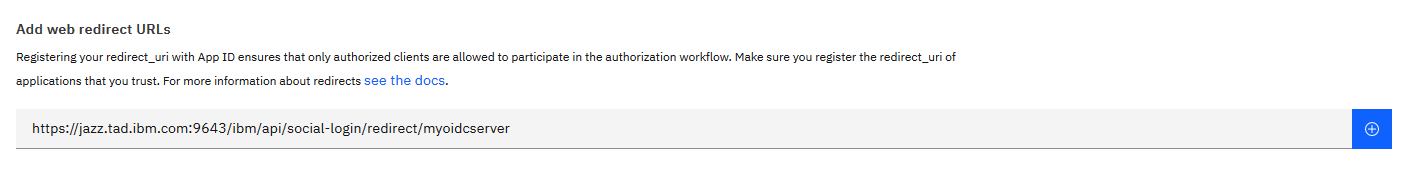 For example, the redirect URL for the oidcLogin configuration example has the following format:
For example, the redirect URL for the oidcLogin configuration example has the following format:
The following error message shows when redirect URL is not set in App ID. Please see Adding redirect URIs for details.
Please see Adding redirect URIs for details.
When you only use IBM ID for user management this is not needed.

Limitations
In this approach the user authentication is further delegated from JAS to App ID and this leads to redirections which some clients cannot do. Following are the limitations- Authenticating with App ID works only for Browser based clients
- Thick Clients (Eclipse, Visual Studio) and Command line utilities can be configured to authenticate via JAS and hence JAS needs to be connected to the own LDAP server or local directory as App ID does not provides LDAP access. Alternatively Client Certificate or Native Password can be considered.
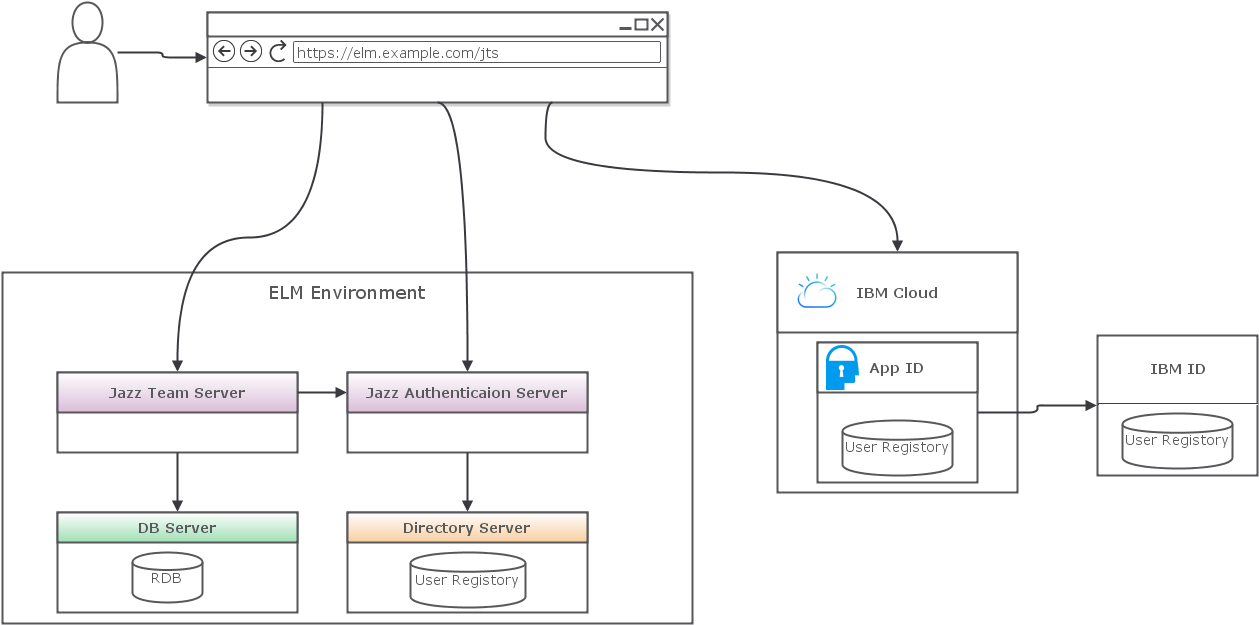
Deployment Pattern
The following diagram depicts the deployment topology and the authentication flow.
Overview of Configuration
Overview of the different steps involved in this configuration.- Configure on App ID
- Configure OIDC Login in liberty in JAS
- Set Redirect URL from JAS in App ID
- Import certificate of App ID in a trust store in JAS
- Add users to Cloud Directory in App ID ( Optional )
Configure on App ID
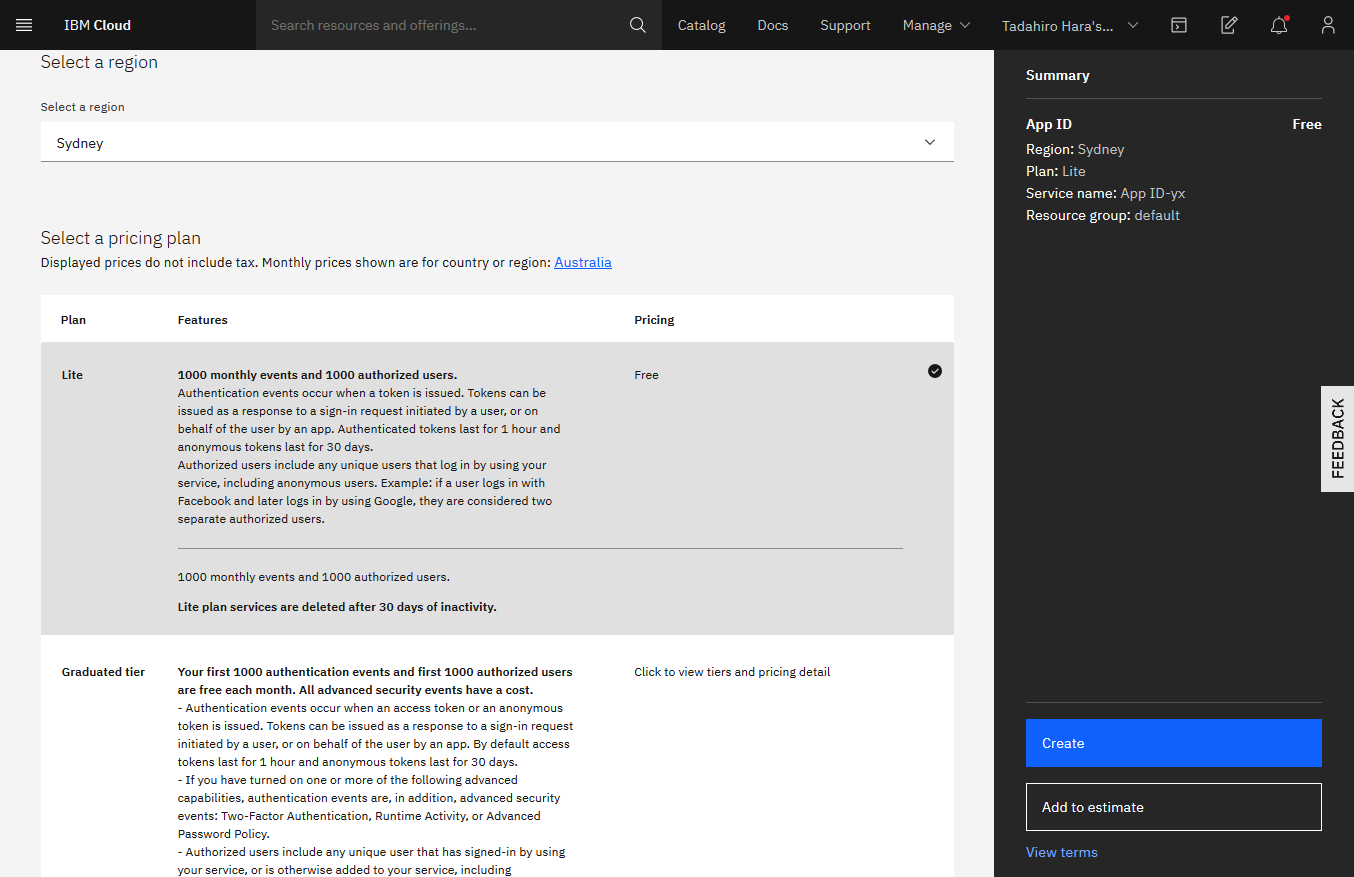
Create App ID instance on IBM cloud
You can deploy App ID instance from catalog in IBM Cloud when you have an account of IBM Cloud. Deploying App ID instance.
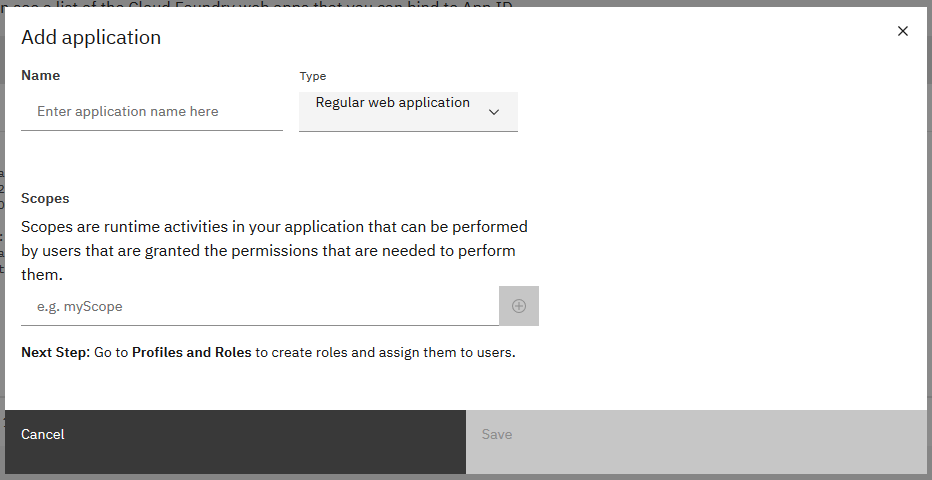
Add Application to App ID
you can add "Application" to get information for liberty OIDC settings. please navigate Application from menu. Adding an application in App ID.
Adding an application in App ID. You can get information for liberty OIDC settings after adding an "Application".
You can get information for liberty OIDC settings after adding an "Application".
{
"clientId": "xxxx1234-1234-1234-xxxx-e18890408990",
"tenantId": "xxxx1234-1234-1234-1234-206ad598442e",
"secret": "XXXXXXXXXXXXMDRkMC00ZTRjLTk1Y2MtYWU4MTIzNmQ2ZDZl",
"name": "JAS",
"oAuthServerUrl": "https://au-syd.appid.cloud.ibm.com/oauth/v4/xxxx1234-1234-1234-1234-206ad598442e",
"profilesUrl": "https://au-syd.appid.cloud.ibm.com",
"discoveryEndpoint": "https://au-syd.appid.cloud.ibm.com/oauth/v4/xxxx1234-1234-1234-1234-206ad598442e/.well-known/openid-configuration",
"type": "regularwebapp",
"scopes": [
"myscope01"
]
}
Configure OIDC Login in liberty in JAS
You need to configure server.xml and appConfig.xml in liberty in JAS to redirect authentication to App ID.- Open the
[JAS_HOME]\wlp\usr\servers\jazzop\server.xmlconfiguration file and add the socialLogin-1.0 , ssl-1.0 - Add the
oidcLoginelement and configure the connection to App ID by referring "Application" information.
| Attribute in oidcLogin | Value from Application Information |
| clientId | {clientId} |
| clientSecret | {secret} |
| authorizationEndpoint | {oAuthServerUrl}/authorization |
| tokenEndpoint | {oAuthServerUrl}/token |
| issuer | {oAuthServerUrl} |
| jwksUri | {oAuthServerUrl}/publickeys |
| scope | {scopes} |
Example of configuration.
<featureManager>
<feature>socialLogin-1.0</feature>
<feature>appSecurity-2.0</feature>
<feature>ssl-1.0</feature>
...
</featureManager>
<oidcLogin id="myoidcserver" displayName="OIDC Login"
clientId="xxxx1234-24a4-4172-ba66-e18890408990"
clientSecret="XXXXXXXXXXXXMDRkMC00ZTRjLTk1Y2MtYWU4MTIzNmQ2ZDZl"
authorizationEndpoint="https://au-syd.appid.cloud.ibm.com/oauth/v4/xxxx1234-1234-47ec-9e28-206ad598442e/authorization"
tokenEndpoint="https://au-syd.appid.cloud.ibm.com/oauth/v4/xxxx1234-1234-47ec-9e28-206ad598442e/token"
issuer="https://au-syd.appid.cloud.ibm.com/oauth/v4/xxxx1234-1234-47ec-9e28-206ad598442e"
jwksUri="https://au-syd.appid.cloud.ibm.com/oauth/v4/xxxx1234-1234-47ec-9e28-206ad598442e/publickeys"
scope="myscope01"
userNameAttribute="email" >
authFilterRef="myoidcAuthFilter" >
</oidcLogin>
<authFilter id="myoidcAuthFilter">
<userAgent id="oidcUserAgent" agent="Mozilla|Opera" matchType="contains"/>
<requestUrl id="pingRequestUrl" urlPattern="/authorize" matchType="contains"/>
</authFilter>
Please see OIDC discovery document and Liberty Topic: Configuring Social Login in Liberty for details
Set Redirect URL from JAS in App ID
You need to set "Redirect URL" of JAS to App ID. please navigate Identity Providers > Manage > Authentication Settings. For example, the redirect URL for the oidcLogin configuration example has the following format:
For example, the redirect URL for the oidcLogin configuration example has the following format:
https://[JAS_Host]:[Port]/ibm/api/social-login/redirect/oidclogin_id
The following error message shows when redirect URL is not set in App ID.
 Please see Adding redirect URIs for details.
Please see Adding redirect URIs for details.
Import a certificate of App ID in a trust store in JAS
You need to import a certificate of App ID in a trust store in JAS or you can see the following error when http request is redirected from App ID.CWPKI0823E: SSL HANDSHAKE FAILURE: A signer with SubjectDN [CN=au-syd.appid.cloud.ibm.com, O=International Business Machines Corporation, L=Armonk, ST=New York, C=US] was sent from the host [au-syd.appid.cloud.ibm.com:443]. The signer might need to be added to local trust store [ibm-team.keystore], located in SSL configuration alias [defaultSSLConfig]. The extended error message from the SSL handshake exception is: [PKIXCertPathBuilderImpl could not build a valid CertPath.].
- import the certificate to the Liberty truststore
[JAS_HOME]\wlp\usr\servers\jazzop\ibm-team.keystorefile, in your browser, go to one of the endpoints specified by the oidcLogin elementau-syd.appid.cloud.ibm.com, and export the certificate. Use a key management tool such as iKeyman or the Java keytool utility to add the certificate to the Liberty truststore file.
Add users to Cloud Directory in App ID (Optional)
When you use Cloud Directory for user management you can add users by referring Add Users.When you only use IBM ID for user management this is not needed.
After configuration
After configuration, when you access to JTS application, your request will be redirect to Login Form in App ID on IBM Cloud.
Related topics:
External links:
Additional contributors:
Contributions are governed by our Terms of Use. Please read the following disclaimer.
Dashboards and work items are no longer publicly available, so some links may be invalid. We now provide similar information through other means. Learn more here.