Configuring ELM Authentication with Multiple Third Party OIDC Providers
Authors: ShubjitNaikBuild basis: Engineering Lifecycle Management 7.0.2 or higher
There are requirements where ELM has to be deployed in an environment for users from different companies to collaborate. And in this scenario the end users would need to authenticate against different IDPs which could be their respective company owned IDPs. Can we configure multiple Identity Providers with IBM Engineering Lifecycle Management Solution?
A general example of this pattern is to configure a Liberty server so that users can authenticate to websites that are hosted on the Liberty server by logging in with their social media account. You can choose from the predefined social media platform configurations, or define your own configuration for any social media platform that is based on the OAuth 2.0 or OpenID Connect standards. You can setup ELM to authenitcate via Jazz Authorization Server (JAS) which is based on WebSphere Application Server Liberty. And using the SocialLogin feature a Liberty server can be configured to further delegate the user authentication to Third Party OIDC Provider. If multiple OIDC Providers are configured to protect a request, Liberty provides a default selection form that offers you the option to choose between the available OIDC providers configured in the Liberty server. Visit Liberty Social Media Selection Form for additional information. The focus on this article is on configuring Multiple Third party OIDC Providers in JAS using the Social Login feature and the Liberty default Social Media selection form.
A general example of this pattern is to configure a Liberty server so that users can authenticate to websites that are hosted on the Liberty server by logging in with their social media account. You can choose from the predefined social media platform configurations, or define your own configuration for any social media platform that is based on the OAuth 2.0 or OpenID Connect standards. You can setup ELM to authenitcate via Jazz Authorization Server (JAS) which is based on WebSphere Application Server Liberty. And using the SocialLogin feature a Liberty server can be configured to further delegate the user authentication to Third Party OIDC Provider. If multiple OIDC Providers are configured to protect a request, Liberty provides a default selection form that offers you the option to choose between the available OIDC providers configured in the Liberty server. Visit Liberty Social Media Selection Form for additional information. The focus on this article is on configuring Multiple Third party OIDC Providers in JAS using the Social Login feature and the Liberty default Social Media selection form.
Configure JAS and User Group Role Mapping
First step is to configure ELM and JAS. You would need to either configure JAS with multiple LDAPs, one each for a Third Party OIDC Provider, or a consolidated LDAP server which has a copy of all the Users from multiple OIDC Providers.- To configure multiple LDAPs in JAS you would need to enable SCIM. Visit Configure Multiple User Registries with JAS and SCIM
- To configure a single LDAP with JAS Visit Configure JAS with an LDAP User Registry
- When configured with SCIM, JTS does the group lookup via the SCIM URL and groups provided under JTS Admin > Advanced Properties >
-
com.ibm.team.repository.service.jts.internal.userregistry.scim.SCIMUserRegistryProviderfor User group to Jazz role mappings
-
- When configured with LDAP, JTS does a group lookup via an ldapsearch Query against the LDAP and group details mentioned under JTS Admin > Advanced Properties >
-
com.ibm.team.repository.service.jts.internal.userregistry.ldap.LDAPUserRegistryProviderfor User group to Jazz role mappings.
-
Configure Social Login in JAS to Redirect to Third Party OIDC Provider
We have the instructions for configuring JAS with a Third Party OIDC Provider documented the the Article Configure ELM Authentication with a Third Party OIDC provider. The high level instructions are :- Create ClientId and Client Secret for JAS on the Third Party OIDC Provider
- Add the redirect URL of format
https://[JAS_HOST]:[Port]/ibm/api/social-login/redirect/[ID] - Enable the feature
socialLogin-1.0in JASserver.xml - Add
oidcLoginelement to configure the connection to OIDC Provider inappConfig.xml - Configure Filters for Non-Web clients
- Configure LDAP in JAS and JTS for User to group role mapping
[JAS_HOME]\wlp\usr\servers\jazzop\appConfig.xml
<featureManager>
<feature>socialLogin-1.0</feature>
<feature>appSecurity-2.0</feature>
<feature>ssl-1.0</feature>
</featureManager>
<oidcLogin id="myoidcserver" displayName="Google OIDC Login"
clientId="[my_client_Id]"
clientSecret="[my_client_password]"
authorizationEndpoint="https://accounts.google.com/o/oauth2/v2/auth"
tokenEndpoint="https://www.googleapis.com/oauth2/v4/token"
jwksUri="https://www.googleapis.com/oauth2/v3/certs"
issuer="https://accounts.google.com"
scope="openid general profile email"
userNameAttribute="email"
authFilterRef="myoidcAuthFilter1">
</oidcLogin>
<authFilter id="myoidcAuthFilter">
<userAgent id="myoidcUserAgent" agent="Mozilla|Opera" matchType="contains"/>
<requestUrl id="myoidcRequestUrl" urlPattern="/authorize" matchType="contains" />
</authFilter>
- The
clientIdandclientSecretare to be generated by your OIDC provider - The redirect URL points to the ID of your configured oidcLogin element and for the sample above the redirect URL is
https://JAS_Host:Port/ibm/api/social-login/redirect/myoidcserver
Configure Multiple OIDC Providers in JAS
The instructions are similar to the previous step. You add anotheroidcLogin element with a unique ID, displayName and Filter.
Here is a sample configuration for multiple OIDC Providers
<featureManager>
<feature>socialLogin-1.0</feature>
<feature>appSecurity-2.0</feature>
<feature>ssl-1.0</feature>
</featureManager>
<oidcLogin id="jas2exampleA"
displayName="Example A OIDC Login"
clientId="exampleAclientid"
clientSecret="exampleAclientpassword"
authorizationEndpoint="https://accounts.example_a.com/o/oauth2/v2/auth"
tokenEndpoint="https://www.apis.example_a.com/oauth2/v4/token"
jwksUri="https://www.apis.example_a.com/oauth2/v3/certs"
issuer="https://accounts.example_a.com"
scope="openid general profile email"
userNameAttribute="email"
authFilterRef="ExampleAAuthFilter" >
</oidcLogin>
<authFilter id="ExampleAAuthFilter">
<userAgent id="ExampleAUserAgent" agent="Mozilla|Opera" matchType="contains"/>
<requestUrl id="ExampleARequestUrl" urlPattern="/authorize" matchType="contains" />
</authFilter>
<oidcLogin id="jas2exampleB"
displayName="Example B OIDC Login"
clientId="exampleBclientid"
clientSecret="exampleBclientpassword"
authorizationEndpoint="https://example_b.com/oidc/endpoint/sample/authorize"
tokenEndpoint="https://example_b.com/oidc/endpoint/sample/token"
jwksUri="https://example_b.com/oidc/endpoint/sample/jwk"
issuer="https://example_b.com/oidc/endpoint/sample"
scope="openid profile email"
userNameAttribute="email"
authFilterRef="ExampleBAuthFilter" >
</oidcLogin>
<authFilter id="ExampleBAuthFilter">
<userAgent id="ExampleBUserAgent" agent="Mozilla|Opera" matchType="contains"/>
<requestUrl id="ExampleBRequestUrl" urlPattern="/authorize" matchType="contains" />
</authFilter>
<oidcLogin id="jas2exampleC"
displayName="Example C OIDC Login"
clientId="exampleCclientid"
clientSecret="exampleCclientpassword"
authorizationEndpoint="https://example_c.com/oidc/endpoint/example/authorize"
tokenEndpoint="https://example_c.com/oidc/endpoint/example/token"
jwksUri="https://example_c.com/oidc/endpoint/example/jwk"
issuer="https://example_c.com/oidc/endpoint/example"
scope="openid profile email"
userNameAttribute="sub"
authFilterRef="ExampleCAuthFilter" >
</oidcLogin>
<authFilter id="ExampleCAuthFilter">
<userAgent id="ExampleCUserAgent" agent="Mozilla|Opera" matchType="contains"/>
<requestUrl id="ExampleCRequestUrl" urlPattern="/authorize" matchType="contains" />
</authFilter>
- The
clientIdandclientSecretare to be generated by each OIDC provider - The redirect URL points to the ID of your configured oidcLogin element and for the sample above the redirect URLs from JAS are
1. https://JAS_Host:Port/ibm/api/social-login/redirect/jas2exampleA 2. https://JAS_Host:Port/ibm/api/social-login/redirect/jas2exampleB 3. https://JAS_Host:Port/ibm/api/social-login/redirect/jas2exampleC
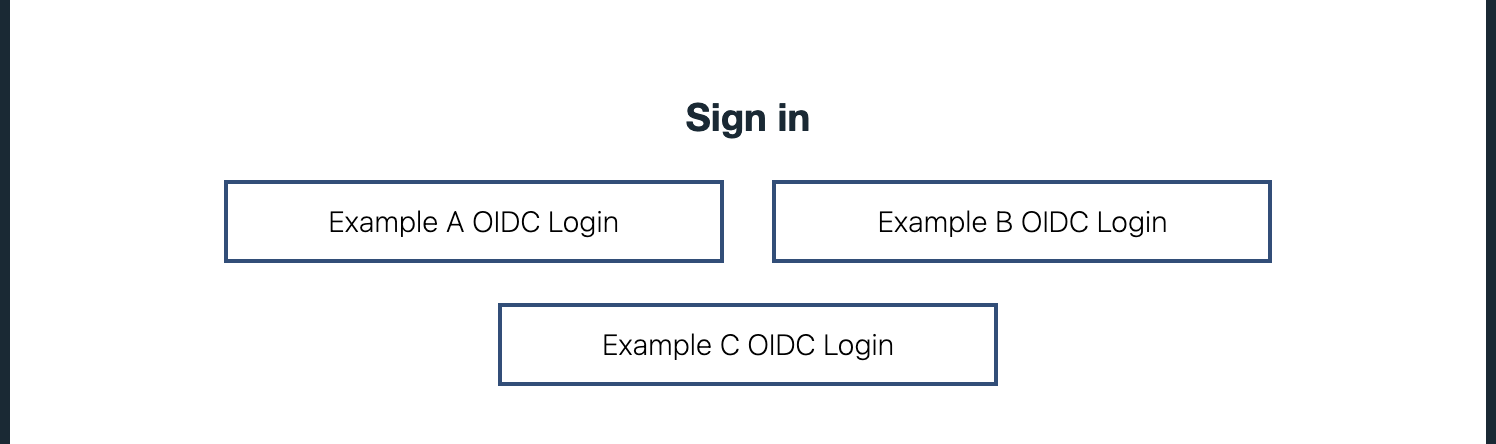
Liberty Default OIDC Providers Selection Form
When multiple OIDC Providers are configured to protect a request, Liberty provides a default selection form that offers you the option to choose between the available OIDC providers configured in the Liberty server. Visit Liberty Social Media Selection Form for additional information. Here is the selection form for the sample provided in the previous step. User can click on the Identity Provider for their Company.
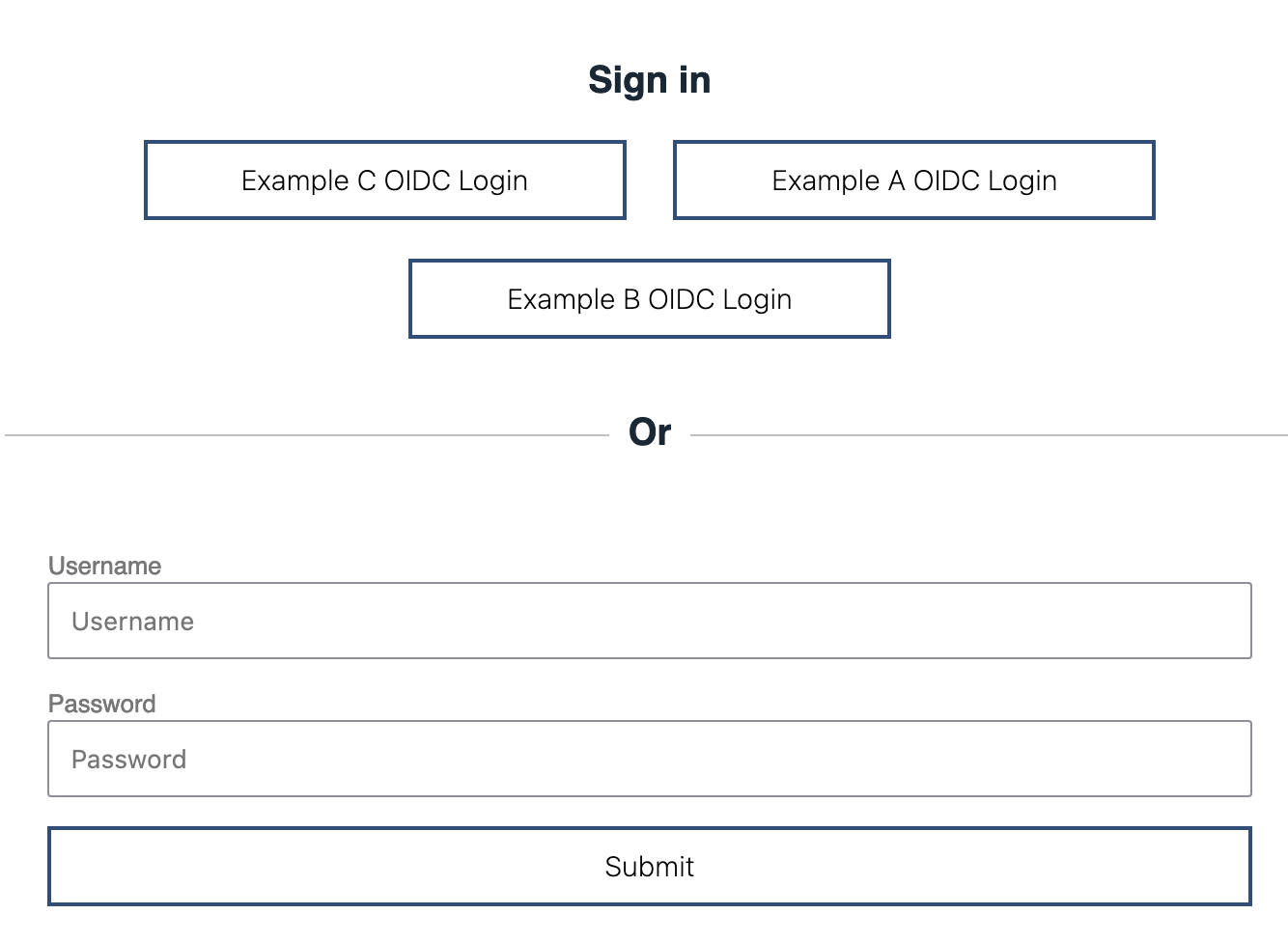
Configure Local Authentication as one of the Providers
You can configure Socal Login Web Application to include Local Authentication in the Selection form. Add the following configuration along with all theoidcLogin configurations:
<socialLoginWebapp enableLocalAuthentication="true" />Here is the updated selection form when Local Authentication is included

Related topics: Configure ELM Authentication with a Third Party OIDC provider, Jazz Authorization Server
External links:
Contributions are governed by our Terms of Use. Please read the following disclaimer.
Dashboards and work items are no longer publicly available, so some links may be invalid. We now provide similar information through other means. Learn more here.