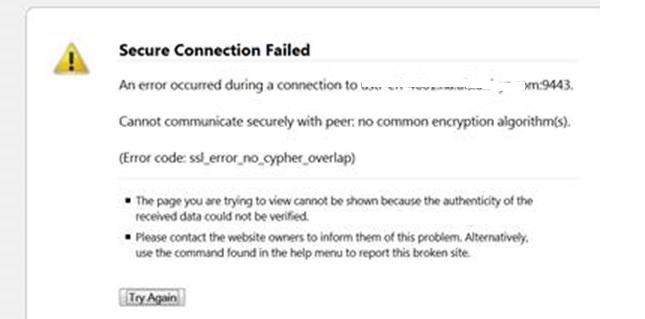
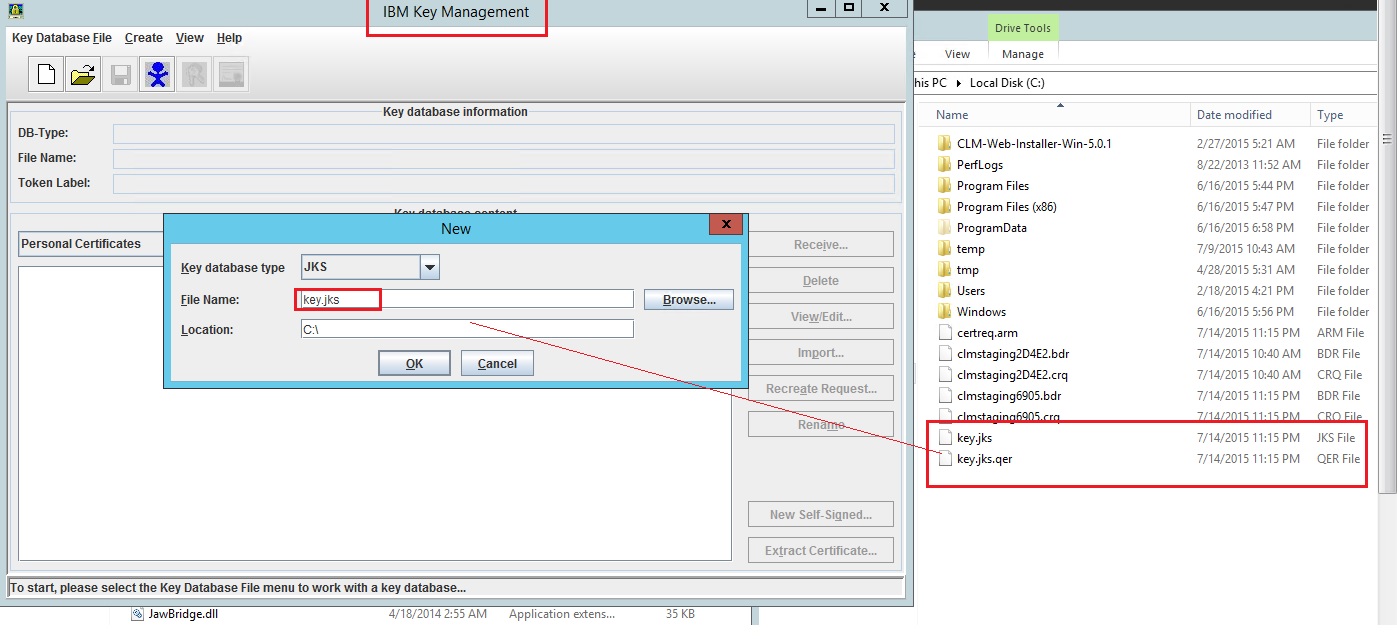
How to request and configure an SSL cerificate for CLM 501 running Apache Tomcat
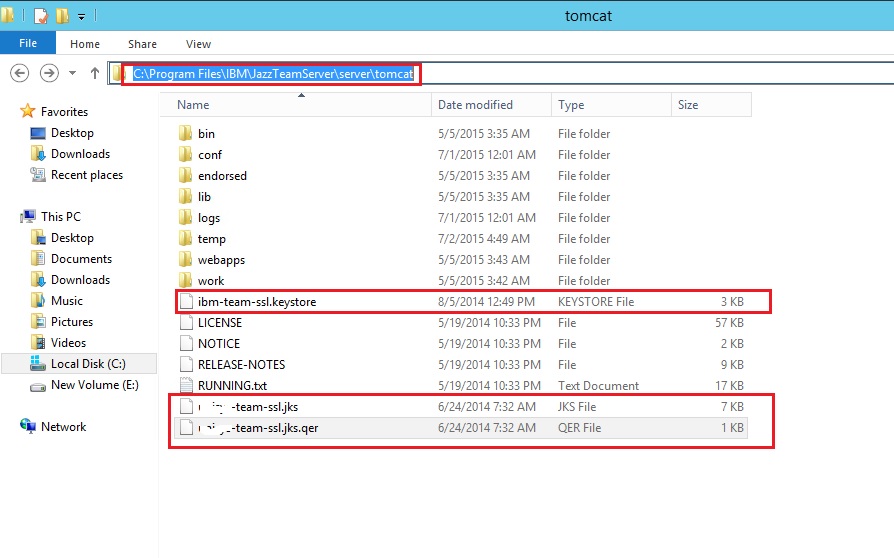
11 answers
Comments
You can confirm the certificate when opening the .jks file in the ikeyman.
Hi - I saw this reference late and tied running the command
As a certificate is normally bound to an FQDN, if you don't change the public URI of the CLM server (i.e. the clients use the same URL to access CLM applications), you don't need to get the certificate re-issued. Just copy the keystore (and the password stash if appropriate) over to the new environment and you are good to go.
Comments
Here we are starting from the scratch as we are moving to a new hardware.
It's quite likely your current certificate was generated by the method detailed in this article.
http://www.ibm.com/developerworks/rational/library/create-server-side-certificates-collaborative-lifecycle-management/
Note that it uses iKeyMan, not keytool. If you want to use keytool, you can follow these steps instead.
http://docs.oracle.com/cd/E19798-01/821-1841/gjrgy/index.html
2 votes
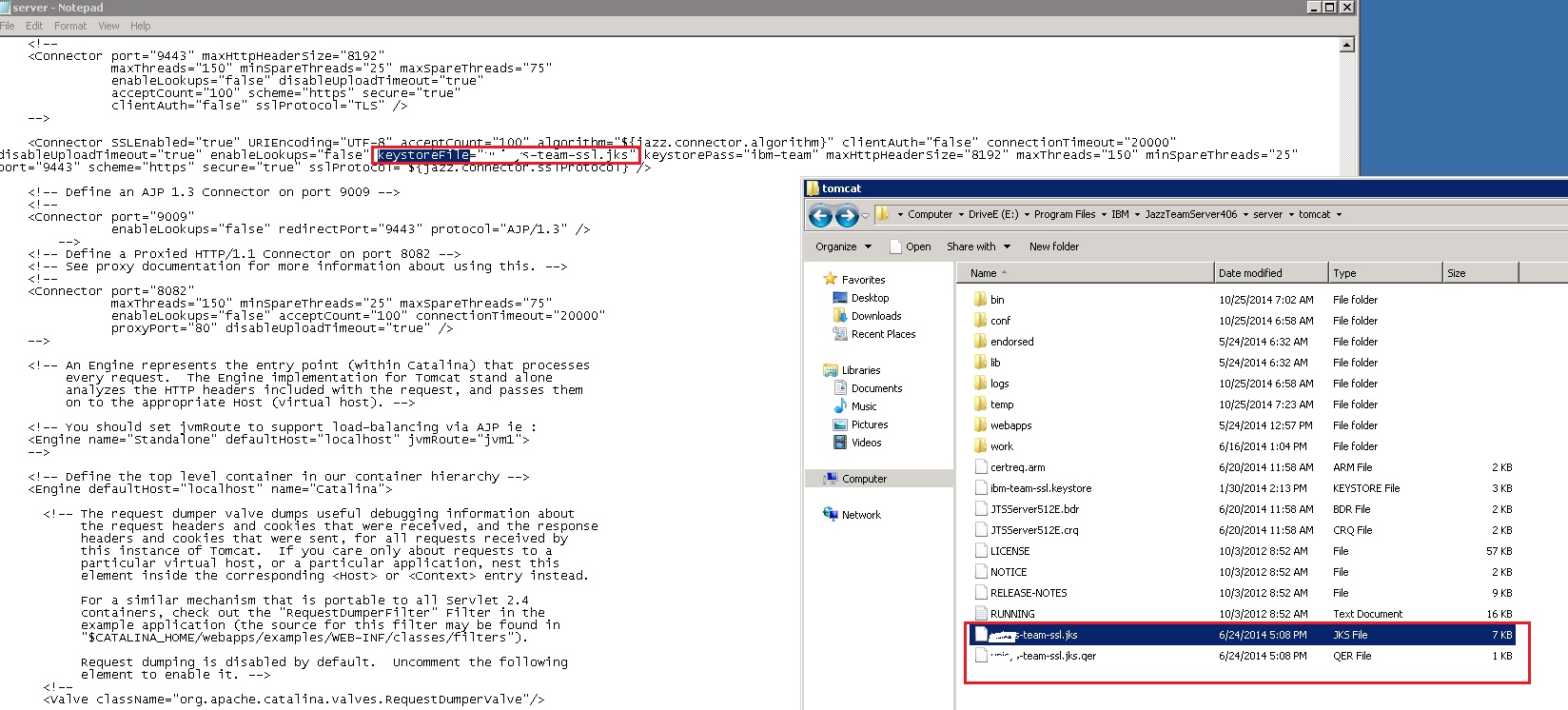
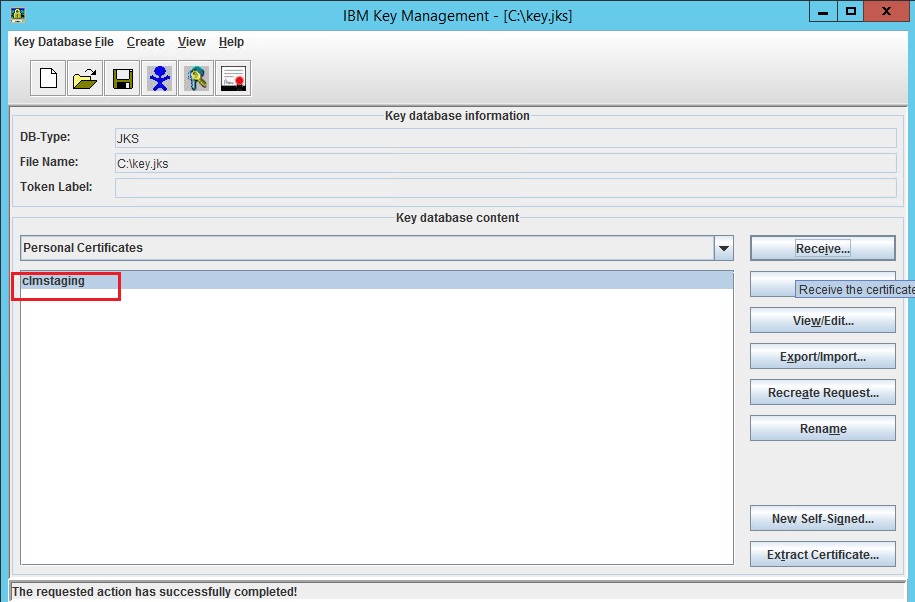
- Now that I have generated the clm_staging_keys.jks file -
- Hope this file can be sent to our CA to get it signed.
- Once we receive the signed certificate back.
- Will be copying the signed certificate back to the tomcat directory.
- In the next step - update the Tomcat - Server.xml file with the new Keyfile name and password.
- Restart the tomcat services.
Comments
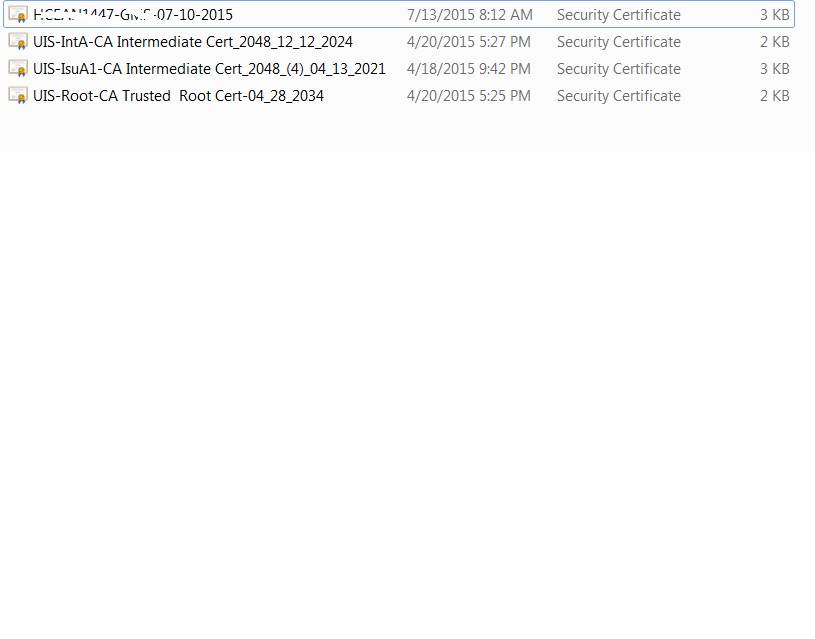
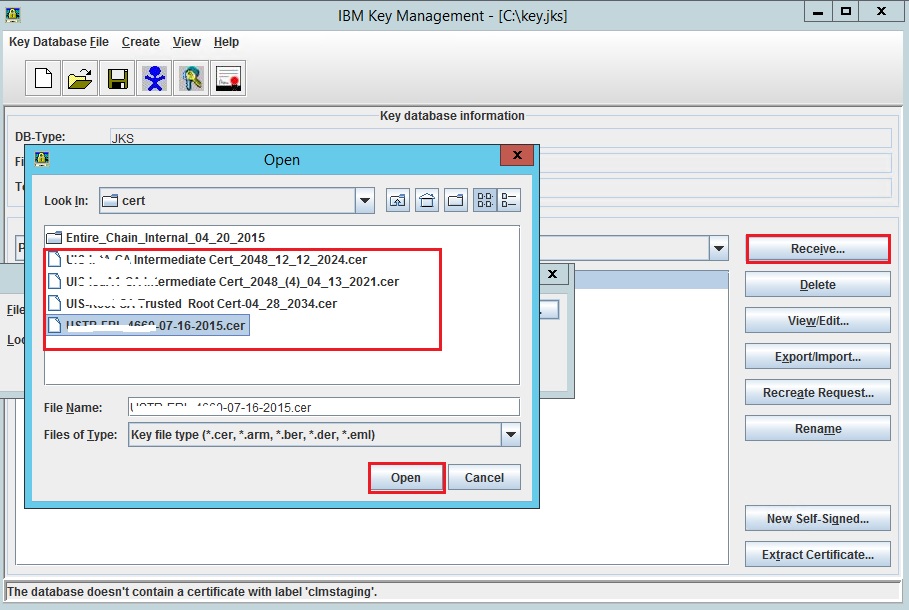
You need to understand what is a key, a certificate, and a key store. The files that you listed are certificates, and you need to import them into the key store. Follow the steps in the following document (see section: Receiving a CA-signed certificate).
http://www-01.ibm.com/software/webservers/httpservers/doc/v1312/ibm/9atikeyu.htm


Comments
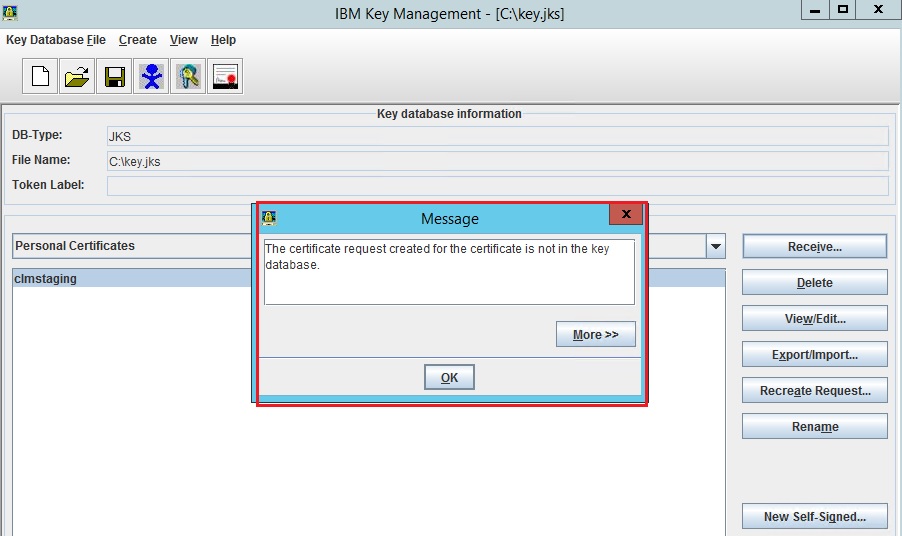
The error is expected as the other certificates are "CA's certificates", not personal certificates. You should follow the instructions in the section "Storing a CA's certificate" in the same document to add them to the key store.
1 vote
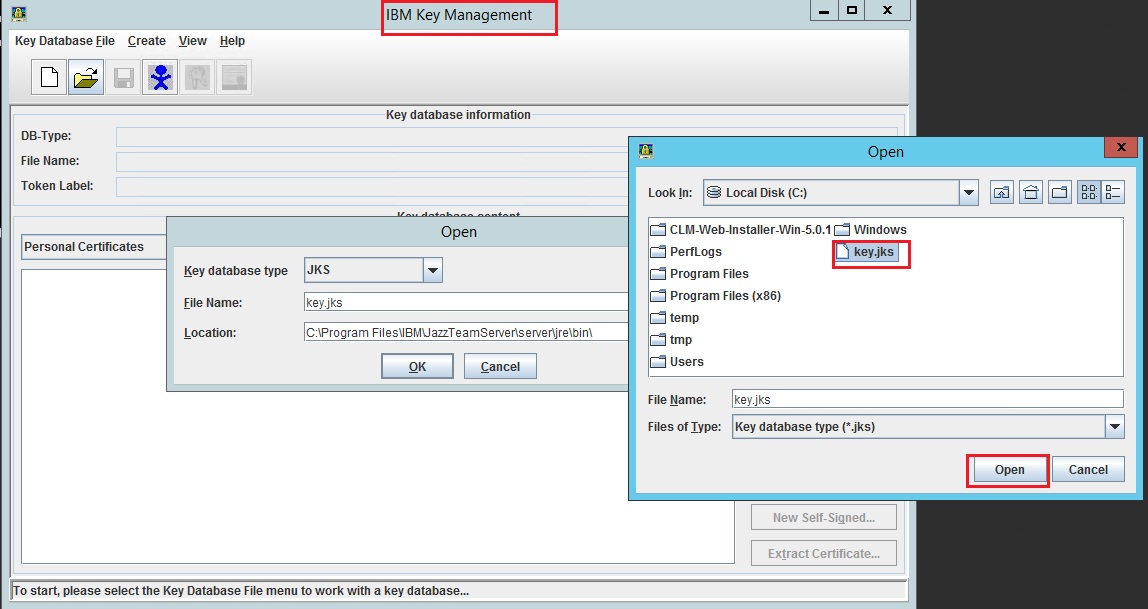
Hi Don,
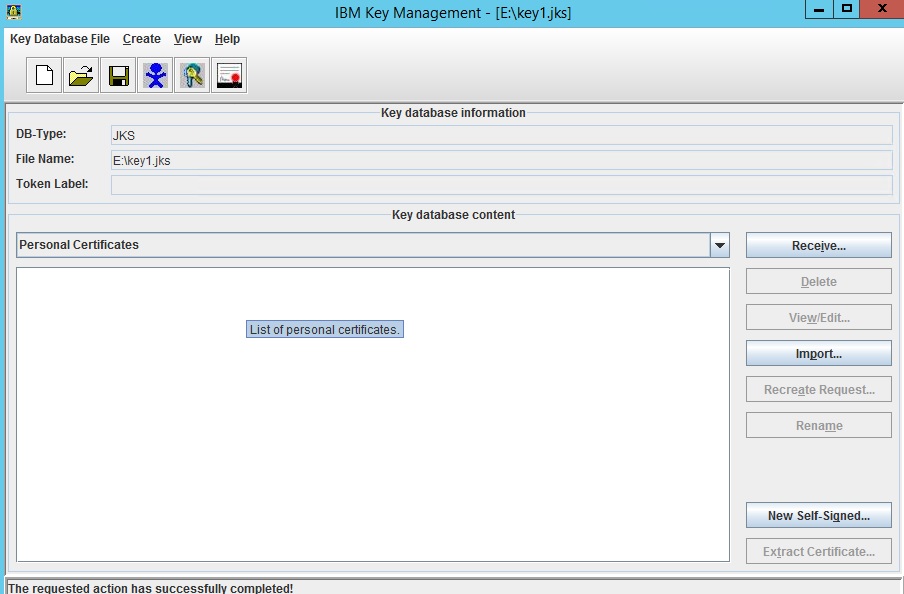
Click on the downward arrow next to "Personal Certificates" and you should see something like this.

1 vote