How to configure CA- Signed Certificate in WAS for RAM
Dear team,
We have a requirement for configuring CA- Signed Certificate in WAS for RAM.

having discussed with our internal Identity management team we ran Ikeyman tool from E:\Program Files\IBM\WebSphere\AppServer\profiles\AppSrv01\bin
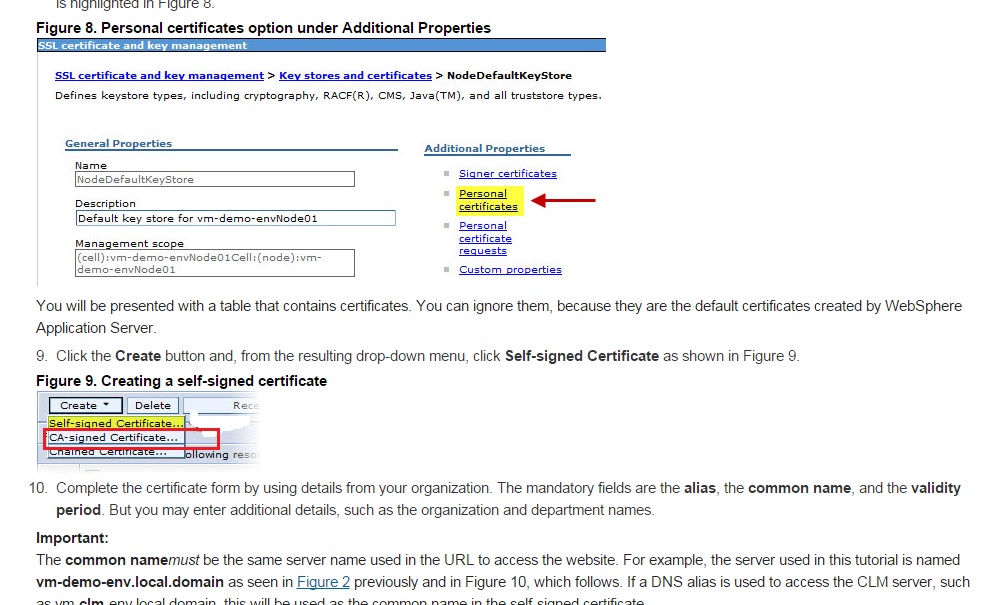
In the IBM Key Management Utility, click on Key Database File and then New.
- Choose Key database type and select JKS. Give the keystore a name such as your_domain.jks.
-
Click the Browse button. Go to
C:\Program Files\IBM\WebSphere\AppServer\profiles\default\etcor to a different location where you want to store your keystore file. - Click OK. Enter a password and click OK.
- Click Create then New Certificate Request to bring up the Create New Key and Certificate Request dialog.
-
Type a Key Label, Common Name, Organization, Locality, State, and select a Country. Select 2048 for Key Size.
- We have send ramqa1certreq.arm file to the CA authority and in return they have send me the below set of files

My question is : How to get this imported into WAS and after that our end-users should be able to browse the RAM URL (https) with out accepting the certificate on each browser.
2 answers
The path I've always taken with WebSphere is [ you should likely start at #4 below ]
-
Go to NodeDefaultKeystore under Keystores [ as you've done ]
- Click on Personal Certificate Requests / New fill out the form
- Send the CSR to the Certificate Authority. You'll likely get back a Base64 encoded file. Put that on your websphere machine somewhere
- Again on NodeDefaultKeystore / Personal Certificates click Receive from Certificate authority
- Provide the path name
- This should import your new certificate in the NodeDefaultKeyStore file. Make sure it shows up there.
- Next go to SSL Configurations, Open NodeDefaultSSL settings
- Choose your CA signed certificate next to "Default server certificate alias"
- Save
Hi,
Finally I could get this working by getting a CSR certificate signed back from our identity management team.
Also by working with IBM Support engineer Dipak Shah was a great help.
Here is the link to follow
1) Create a new certificate request
Navigate to the path where the file got created and send it to the Identity Management Team and get it signed back. We have tried using Internal certificate key
Note: Make sure you point the file name under any drive with .cer extension.
2. Next step is to receive the SSL cert
3. Replace the old one with new one
http://www14.software.ibm.com/webapp/wsbroker/redirect?version=phil&product=was-nd-dist&topic=tsec_sslreplaceselfsigncertBased on the import we did on our QA enviornment it worked fine with us.