Configure CA and Self-Signed Certificates in Liberty or IHS for ELM Applications 7.0.3
Authors: ShradhaSrivastavBuild basis: ELM 7.0.3
ELM 703 is shipped with Java 11 which no longer ship Ikeyman utility to manage certificate and keystore using GUI.
This article will share sample commands that can be used in place of ikeyman to create or generate new keystore and manage CA certificates.
In order to resolve these errors, you can: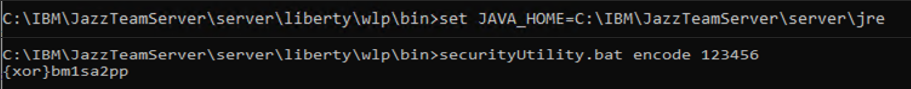
 This concludes the creation of the self signed certificate. The certificate is now in the keystore keystore.p12. After creating (or updating) the keystore, configure the application server to use it by updating the server.xml file as suggested above.
This concludes the creation of the self signed certificate. The certificate is now in the keystore keystore.p12. After creating (or updating) the keystore, configure the application server to use it by updating the server.xml file as suggested above.
Generate certificate Request
To get a CA Certificate you have to generate a certificate request from your keystore. See an example below. The generated file certreq.csr is later used with your CA to receive the final certificate.
How the process works is dependent on the CA.
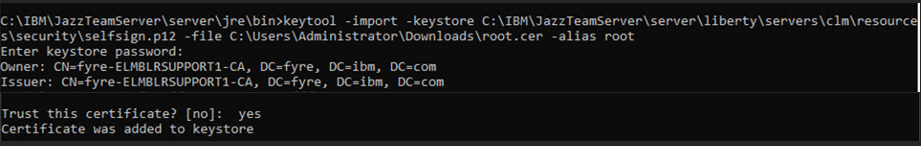
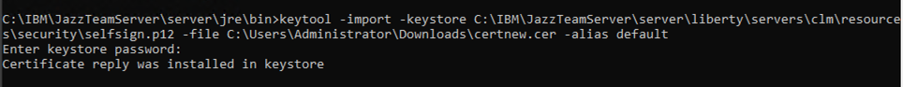
Note:- The intermediate and root certificate should have different alias name, but the signed certificate should be imported with the same alias that was used while creating a certificate pair. After importing all three certificates you should see : "Certificate reply was installed in keystore" message.
Understanding SSL Certificates
All applications which run on HTTPS via the web require a Security Certificate, or Public Key Certificate. This is used to validate that the data is coming from a trusted source. The security certificate bundled with the Jazz Team Server and ELM applications is signed to localhost. As soon as the application is accessed with a URL other than localhost (for example, hostname or IP address), the browser will present the following errors:- The security certificate presented by this website was not issued by a trusted certificate authority.
- The security certificate presented by this website was issued for a different website's address.
- The security certificate was self-signed, meaning that the server being accessed created the certificate, and
- The security certificate was created for localhost, and you are accessing the server using a different hostname, IP address or the appropriate Public URI.
In order to resolve these errors, you can:
- Purchase a certificate from a well-known trusted Certificate Authority and install it.
- If you do not need encryption, configure the server for HTTP rather than HTTPS access.
- Configure the browser to ignore or accept this invalid certificate
Configure Liberty Profile
The Application server needs to be configured to pick up a valid certificate. For Liberty Profile, the certificate needs to be configured in the file[ServerInstallDir]\JazzTeamServer\server\liberty\servers\clm\server.xmlThe entry keystore is, where the certificate is configured. By default, the entry looks like
<keyStore id="defaultKeyStore" location="ibm-team-ssl.p12" type="PKCS12" password="{xor}Nj0ycis6PjI="/>
The location defines the path and name of the keystore. The keystore shipped with the product [ServerInstallDir]\JazzTeamServer\server\liberty\servers\clm\resources\security\ibm-team-ssl.p12Please see the documentation for the keystore entry for more options. You can change the path to a different keystore file. You can place your keystore file into the same folder and just rename the location. The password is encrypted. The type of the keystore can be different based on choice e.g. PKCS12 or JKCS. See the documentation. It is best practice to always provide the keystore type when operation on the keystore. After changing the server.xml settings restart the server.
Encrypt the password for a new key store
If you use a new keystore, the keystore is created with a password. The password has to be provided in the keystore entry. You can encrypt the password to be able to put it input the server.xml. See the description how to encrypt the password. See the image below.
Server name for the certificate
The certificate needs to contain the information about the server name. The server name is usually a unique name containing the fully qualified domain name. Examples would be- elmserv1.fyre.ibm.com
- elm.example.com
- elmserv1.fyre.ibm.com equals to
-dname CN=elmserv1,DC=fyre,DC=ibm,DC=com
- elm.example.com equals to
-dname CN=elm,DC=example,DC=com
keytool command
The new tool for working with certificates is keytool. The keytool can be found in a Java JRE folder. As an example it is shipped with ELM server in the folder[ServerInstallDir]\JazzTeamServer\server\jre\bin\. Tip: To work with the keytool copy the path to the keytool and keep it in an editor. Open a console in a folder you want to use to store your work. You can now use
[ServerInstallDir]\JazzTeamServer\server\jre\bin\keytool [Parameters]to run the keytool. The files involved in the work can all be kept in the dedicated folder. See the next paragraphs for examples how to use keytool
Create a new keystore with self-signed Certificate
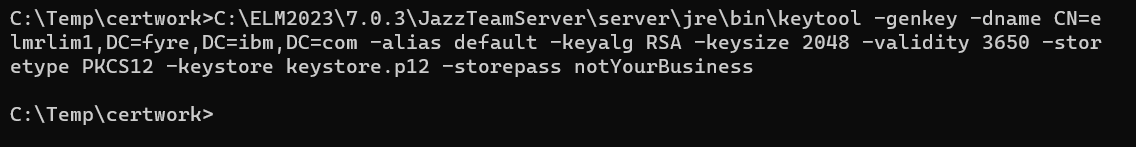
It is possible to create a self signed certificate. Todays browser will not trust a self signed certificate, but accept it if asked to. A self signed certificate is interesting, because it can be locally created without depending on a Certificate Authority (CA). The command requires several parameters such as the keystore name and type to use. As an example the command below creates a new self signed certificate in the file keystore.p12.[ServerInstallDir]\JazzTeamServer\server\jre\bin\keytool -genkey -alias default -keyalg RSA -keysize 2048 -storetype PKCS12 -keystore keystore.p12 -validity 3650You will be prompted for some information such as a password and additional data. See an example below. The parameters needed are the password and the name. All other entries can be left blank. The password will be requested twice, if the keystore does not exist.
Password: ********* What is your first and last name? elmserv1.fyre.ibm.com What is the name of your organizational unit? SW What is the name of your organization? IBM What is the name of your City or Locality? Rochester What is the name of your State or Province? MassachusettsTo avoid having to deal with the prompt, it is possible to provide the parameters required in the command. The example below will perform the creation without prompt.
[ServerInstallDir]\JazzTeamServer\server\jre\bin\keytool -genkey -dname CN=elmserv1,DC=fyre,DC=ibm,DC=com -alias default -keyalg RSA -keysize 2048 -validity 3650 -storetype PKCS12 -keystore keystore.p12 -storepass *********
 This concludes the creation of the self signed certificate. The certificate is now in the keystore keystore.p12. After creating (or updating) the keystore, configure the application server to use it by updating the server.xml file as suggested above.
This concludes the creation of the self signed certificate. The certificate is now in the keystore keystore.p12. After creating (or updating) the keystore, configure the application server to use it by updating the server.xml file as suggested above.
To Configure A CA Certificate
For a real certificate that is also trusted by servers and browsers, it is necessary to request a certificate from a CA. Then this request is sent to a CA and the CA provides the valid certificate to you. Generate certificate Request
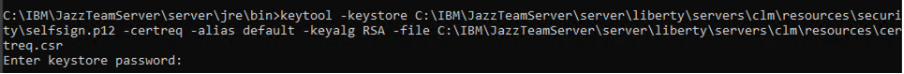
To get a CA Certificate you have to generate a certificate request from your keystore. See an example below. The generated file certreq.csr is later used with your CA to receive the final certificate.
How the process works is dependent on the CA.
[ServerInstallDir]\JazzTeamServer\server\jre\bin\keytool -certreq -alias default -keyalg RSA -file certreq.csr -storetype PKCS12 -keystore keystore.p12 -storepass *********See more examples below.
keytool -keystore keystore.p12 -certreq -alias default -keyalg RSA -file certreq.csr -storepass 123456


Use the certificate request with the CA authority
The generated file certreq.csr is used with your CA to receive the final certificate. How the process works is dependent on the CA.Import/Receive Certificate and Add it to Keystore
The CA provides with a signed or CA certificate for the server. The signed or CA certificate is received or can be downloaded. Obtain the signed or CA certificate. There can be different formats and file names. In this case the certificate is a file named cert.der The CA also provides with- A root certificate
- An intermediate certificate.
[ServerInstallDir]\JazzTeamServer\server\jre\bin\keytool -import -alias inter -file caintermediatecert.der -keystore keystore.p12 -storepass ********* [ServerInstallDir]\JazzTeamServer\server\jre\bin\keytool -import -alias root -file carootcert.der -keystore keystore.p12 -storepass ********* [ServerInstallDir]\JazzTeamServer\server\jre\bin\keytool -alias default -file cert.der -keystore keystore.p12 -storepass *********


Note:- The intermediate and root certificate should have different alias name, but the signed certificate should be imported with the same alias that was used while creating a certificate pair. After importing all three certificates you should see : "Certificate reply was installed in keystore" message.
Using IKEYCMD CLI
As IBM HTTP Server (IHS) still bundles Java 8, you can use ikeyman(GUI) or gskcmd (also known as iKeycmd) to manage certificate and keystores. For more please refer to ConfigureCACertificatesRelated topics: Deployment web home, Keytool Guide
External links:
Additional contributors: ShradhaSrivastav, Ralph Schoon
Contributions are governed by our Terms of Use. Please read the following disclaimer.
Dashboards and work items are no longer publicly available, so some links may be invalid. We now provide similar information through other means. Learn more here.