How to set up distributed CLM for SPNEGO / kerberos
Hi All,
I just wanted to share a simple approach on how to configure SPNEGO on WAS for CLM so that there is some live samples available to the users as it can be quiet complex. This will enable your users to access CLM on the web without having to log in simply "reusing" their windows credentials.
First step is to determine your users entry point. The first server address is the one the intercept will try to get a ticket for. If you have a separate HTTP server in front of your WAS server(s) then this is probably the CNAME you should find. If you have a loadbalancer in front of the HTTP server then this is probably your first point. If you dont use loadbalancer or HTTP server then your entry point is your server or servers if distributed.
Find the ip or ip's of your entry point and in a cmd line run nslookup "your.ip.address" to find the network name this machine resolves to. Be aware that a server can have many aliases but its this name you should use.
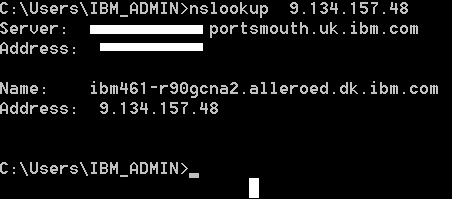
Second step is to get a network user and its password.
Third step is to create a keytab file. this must be done by a person with the right privileges on the network. Ususally a network admin.
sample single entry point (http server or loadbalancer or single WAS):
ktpass -princ HTTP/computername.yourdomain.net@YOURDOMAIN.NET -mapUser networkuser@yourdomain.net -mapOp set -pass networkuserpassword -pType KRB5_NT_PRINCIPAL -out C:\temp\TEST-CLM.keytabsample multiple (distributed with no http server or loadbalancer) - notice the slight changes from the first to subsequent commands
ktpass -princ HTTP/server1.yourdomain.net@YOURDOMAIN.NET -mapUser networkuser@yourdomain.net -mapOp set -pass networkuserpassword -pType KRB5_NT_PRINCIPAL -out C:\temp\TEST-CLM.keytab
ktpass -princ HTTP/server2.yourdomain.net@YOURDOMAIN.NET -mapUser networkuser@yourdomain.net -mapOp add -pass networkuserpassword -pType KRB5_NT_PRINCIPAL -in C:\temp\TEST-CLM.keytab -out C:\temp\TEST-CLM.keytab
ktpass -princ HTTP/server3.yourdomain.net@YOURDOMAIN.NET -mapUser networkuser@yourdomain.net -mapOp add -pass networkuserpassword -pType KRB5_NT_PRINCIPAL -in C:\temp\TEST-CLM.keytab -out C:\temp\TEST-CLM.keytab
Fourth step is to create a kerberos file based on your keytabfile. Luckily websphere can do this for you.
Copy your keytab file to a new folder in D:\IBM\WebSphere\AppServer\keytab
Start a command prompt elevated (run as admin)
Run wsadmin command:
cd D:\IBM\Websphere\Appserver\profiles\Appsrv01\bin\ wsadmin.bat -user yourwasadmin -password <passw0rd> wsadmin> $AdminTask createKrbConfigFile {-krbPath D:\IBM\WebSphere\AppServer\kerberos\TEST.config -realm YOURDOMAIN.NET -kdcHost yourdomain.net -dns yourdomain.net -keytabPath D:\IBM\WebSphere\AppServer\keytab\TEST.keytab}This will create the kerberos file TEST.config in D:\IBM\WebSphere\AppServer\kerberos
The keytab and the kerberos config file must be copied to JTS server, RTC server and RQM server as a minimum.
Start by testing your solution on the JTS server:
log in to WAS admin console.
navigate to security->global security under authentication expand Web and SIP security.
under single sign on Domain name should be set to "YOURDOMAIN.NET"
when you confirmed go back to web and SIP security and click SPNEGO web authentication.
select your 2 files and click apply.
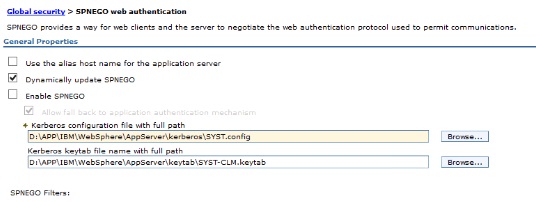
After applied we must add the filter:
Click new and add your entry point server here. If you are distributed with no HTTP servers you only need to add the name of the machine you are currently configuring:
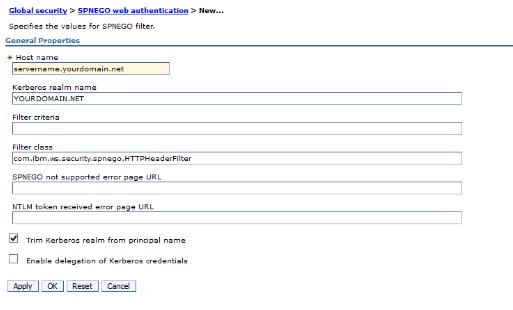
Remember to select the Trim Kerberos option. The click "ok"
Finally on the SPNGO page select the "Enable SPNEGO" to test your solution. also remember to add the fallback in case the authentication fails. finally click ok an save to master configuration.
Step 5 is to test your implementation. To do so you should not user a browser on the same machine as where your WAS is installed. Use another machine. From this machine open a browser (say FireFox). In firefox address bar go to about:config this is because we need to add this domain as trusted. If you use Internet Explorer the site must be added to trusted sites and under Internet Options->advanced-security setting make sure Enable Integrated Windows Authentication (requires restart) is selected.
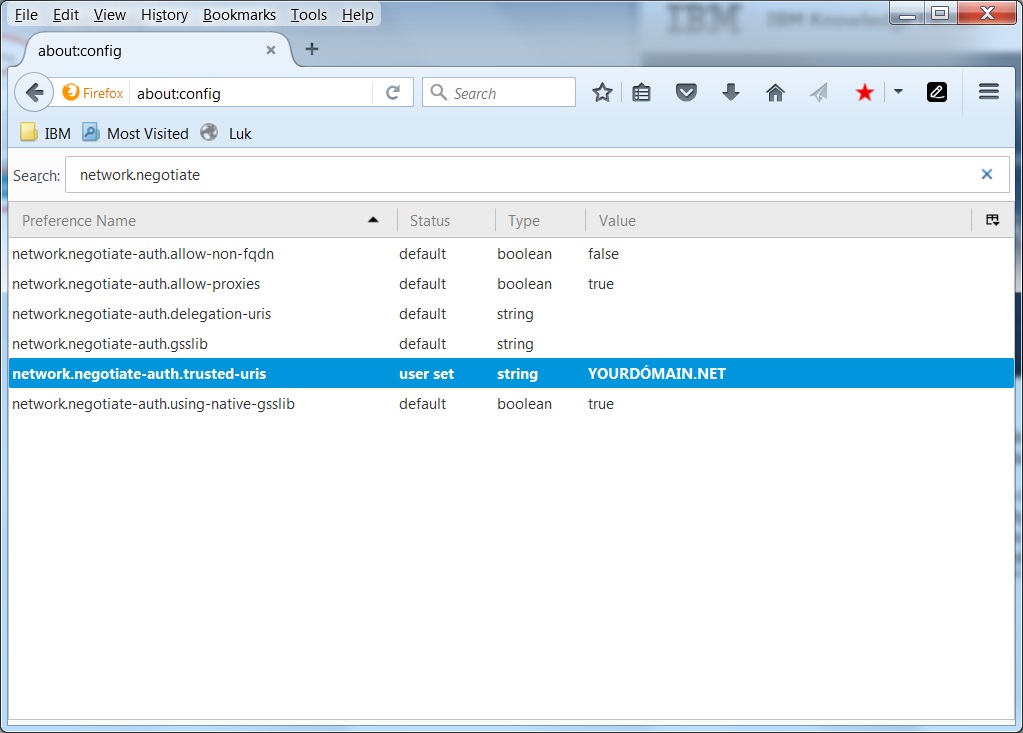
Now navigate to your application https://yourclm.yourdomain.net/jts and you should be logged in automatically.
Subsequent remember to add the files to RTC servers and RQM server or users would not be logged in if they access this directly from a link when they dont have a security token.
Troubleshooting:
If you used an alias you can try ticking of the "you the alias hostname"
If its just not working you can add
=info: com.ibm.ws.security.spnego.=all
under the Troubleshooting->Logs and Trace->change log detail level in your WAS console. This will provide some more details of the SPNEGO errors in your systemout.log
Hope this makes a good supplement to the official documentation
2 answers
Consider requesting access to the deployment Wiki to publish there. Drop me an e-mail if you like to.
Comments
Next time please ask a question and then answer the question with your answer. That way a moderator can accept your answer and you get credited.
Yes yes I know - ordnung muss sein :-)
I will remember the next time.
Now I got the credits Kim 8)
This should really be in the deployment wiki if we don't already have a page for this topic.
Just adding - if you are running enterprice builds and you run into this error:
In WAS admin console navigate to Global Security->Web and Sip security->Single Sign on (SSO) and remove the flag "Set security cookies to HTTPOnly to help prevent cross-site scripting attacks "ERROR: CRJAZ0096E You are attempting to connect to /jazz/jauth-issue-token by using an insecure http protocol.
Try this protocol: https.#