Can a Self-Signed cert support an alias?
For example, the FQDN of the server is apsmxgd-omrjts.devnet1.hill.af.mil, and we have an alias "jts.devnet1.hill.af.mil". We would, therefore, like a certificate to be valid for the following addresses:
apsmxgd-omrjts.devnet1.hill.af.mil
apsmxgd-omrjts
jts.devnet1.hill.af.mil
jts
Does anyone have instructions on how to create such a self-signed cert?
Thanks,
Dave
Accepted answer
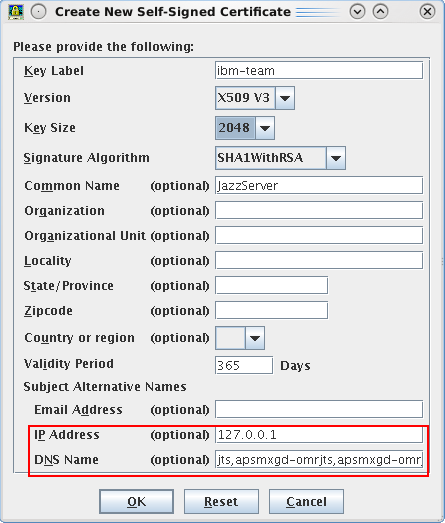
And the resulting certificate would look like this in Firefox.

If you have Java 7 installed, it's said that you can also use the keytool command with -ext option to add this property. I did not verify this though.
http://stackoverflow.com/questions/8744607/how-to-add-subject-alernative-name-to-ssl-certs
http://serverfault.com/questions/605843/unable-to-generate-certificate-with-subject-alternate-name-using-java-1-7-keytoo
Comments
The thing that was hanging me up was that the SAN list must also include the main server name. So it had to be:
apsmxgd-omrjts.devnet1.hill.af.mil,apsmxgd-omrjts,jts
For a bit, I was still receiving the address mismatch error even though the Common Name contained the FQDN. Once I added the FQDN to the SAN list, it worked!
...Either that, or I got lucky with some other thing :)
One other answer
https://www.freessl.com/
Notice that the certificate is issued to "www.chainedssl.com".
In your case, all the certificate needs to do is to identify itself as "the server", whatever the CN you use for it does not matter.
Comments
The reason it works for multiple websites is that the SAN (Subject Alternative Name) contains the following:
DNS Name=www.freessl.com
DNS Name=freessl.com
DNS Name=www.chainedssl.com
DNS Name=chainedssl.com
However, I do not see a way to specify the SAN property in iKeyMan or WAS. That is why I am asking this question here.
Comments
Donald Nong
Dec 04 '15, 2:33 a.m.What is the purpose of doing so? Strictly speaking, a self-signed certificate is not a "valid" one because it cannot be trusted. A browser will always prompt a warning when receiving a self-signed (i.e. untrusted) certificate. A certificate is just an identity. It seems like you want to use a single certificate as multiple identities? I can't understand the reason behind this.
Dave Evans
Dec 07 '15, 8:38 a.m.The purpose is that we would like to be able to use the alias, and even the hostname only, since that would be easier than typing out our ugly URL. If we had it to do over, the original URL would have been much shorter. But since the Public URL is difficult to change, and would produce many broken links, we would rather create a cert which is valid for both the FQDN and also just the DN.
As I said before, this is for our own private web network (NOT ON THE INTERNET), a stand-alone network. That said, we can readily distribute our self-signed cert to all trusted key stores so that people don't receive the warning. The problem here is that if we don't have a certificate which is valid for both addresses, then they will still receive an address mismatch warning for the cert.