How to configure liberty for certificate login
Accepted answer
How to configure ELM on Liberty for Certificate failover (for smart card, build users and other)
You need basically 3 steps: <o:p> </o:p>
1) create a certificate and import it to elm server <o:p> </o:p>
2) update apps to failover to certificates <o:p> </o:p>
3) configure liberty to map certificates to users <o:p> </o:p>
Create a certificate and import it <o:p> </o:p>
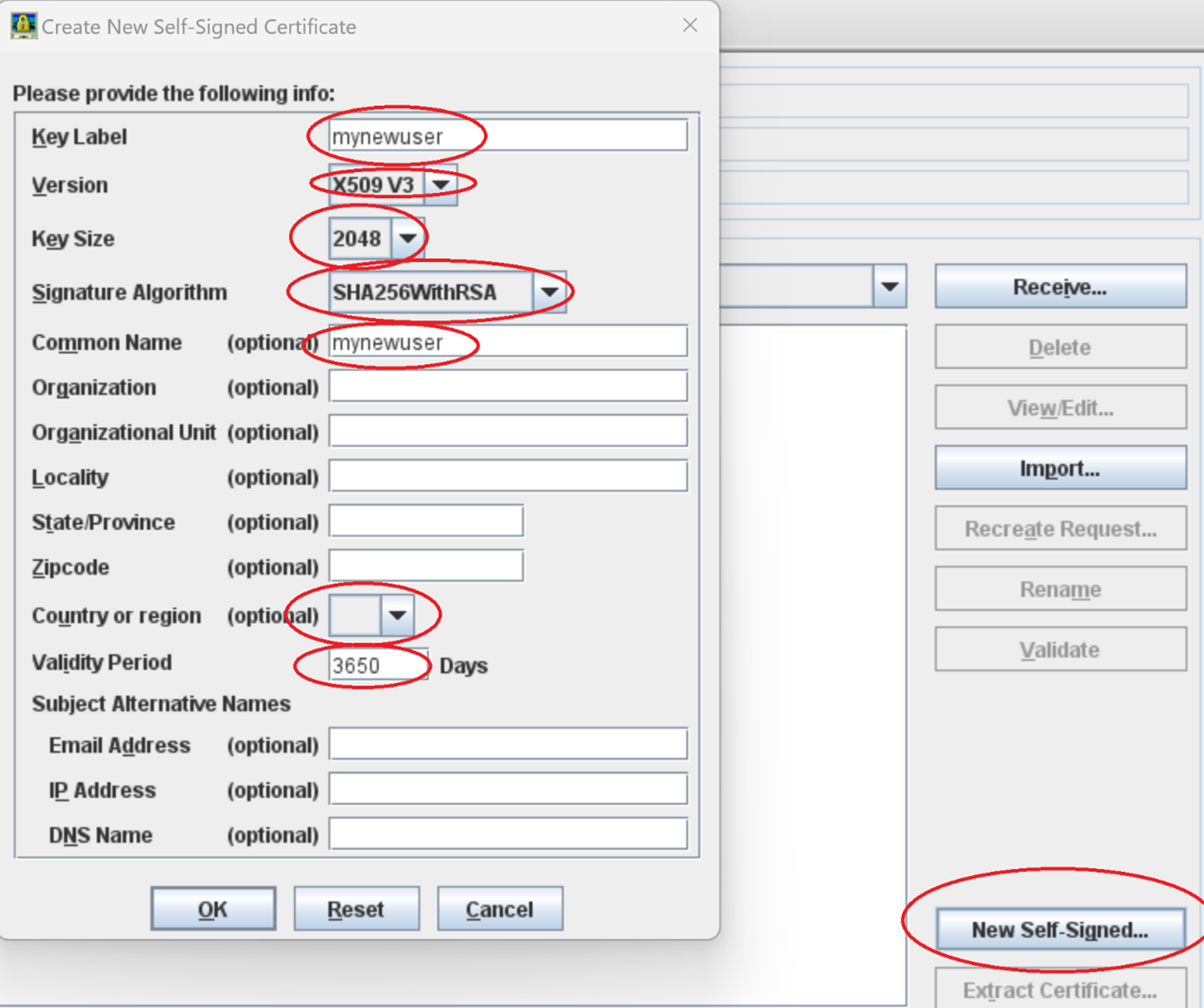
In ikeyman create a new self signed certificate under signer certificates. Name the certificate after the users login id. <o:p> </o:p>
In our sample we use a user with sAMAccountName=”mynewuser” from the AD. Your AD id field could be different. <o:p> </o:p>
We are also going to reuse the existing keystore used by Liberty. <o:p> </o:p>
Run ikeyman (JazzTeamServer702\server\jre\bin\ikeyman.exe as admin <o:p> </o:p>
Create a new certificate to be used for build toolkit for instance called mynewuser.p12 <o:p> </o:p>
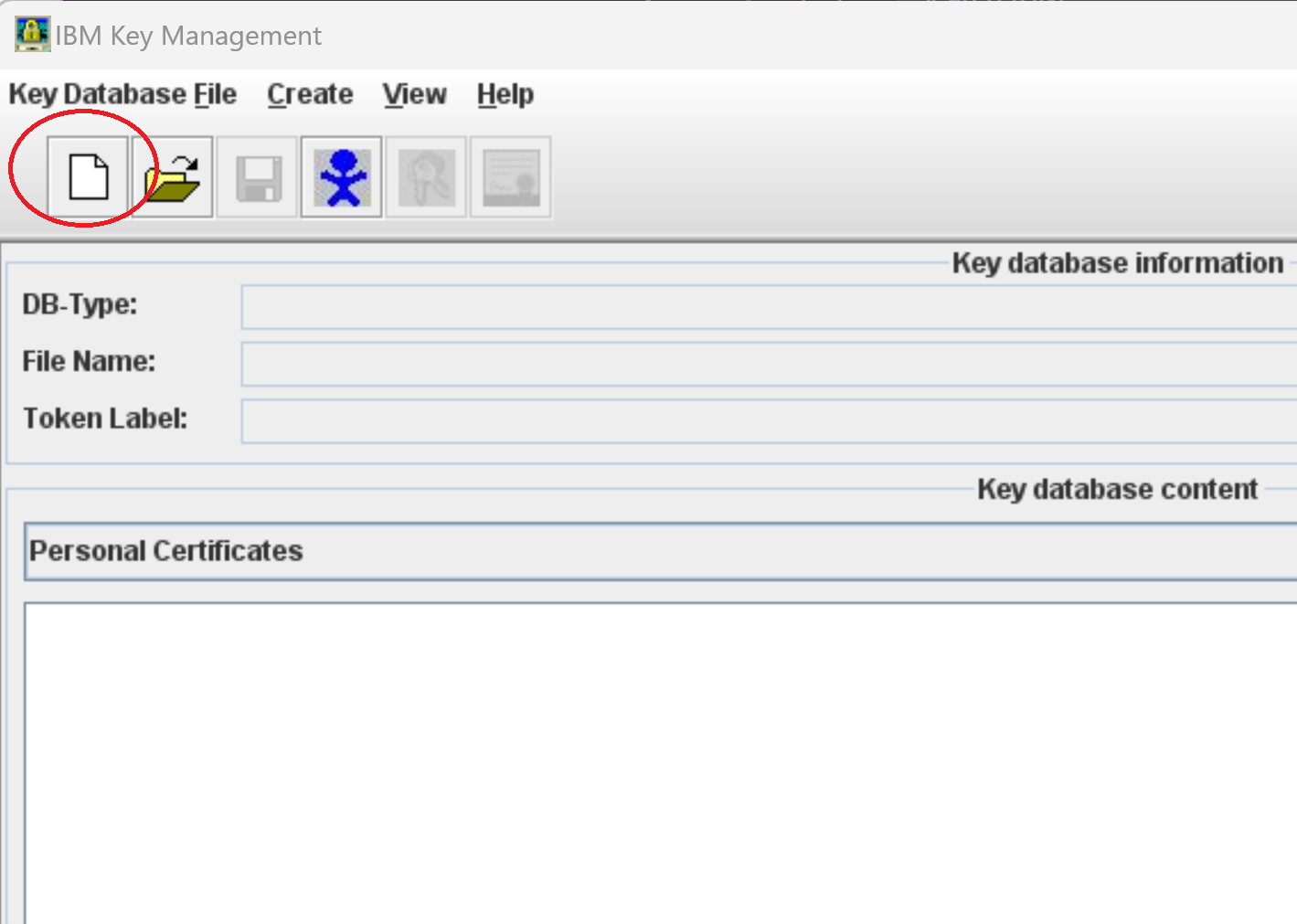
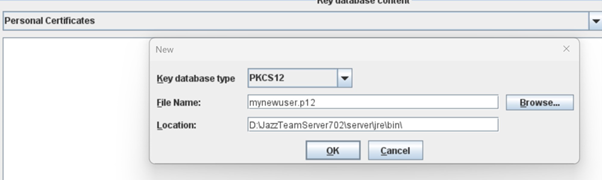
Create a new self signed certificate matching the sAMAccountname from the AD <o:p> </o:p>
and open the \JazzTeamServer702\server\liberty\servers\clm\resources\security\ibm-team-ssl.p12 <o:p> </o:p>
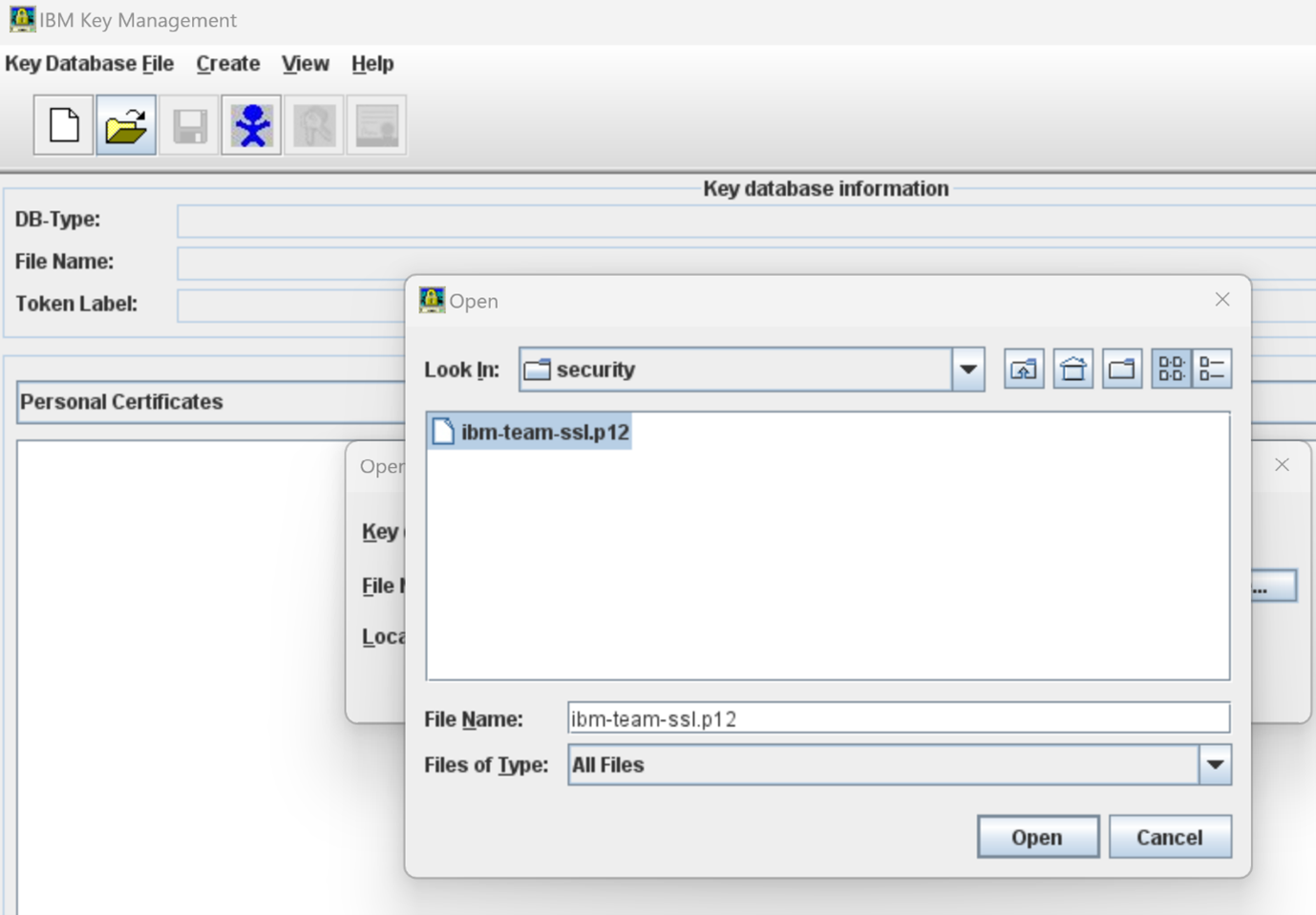
Create a new self signed certificate <o:p> </o:p>
Your keystore should look like this: <o:p> </o:p>
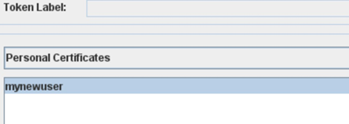
After this you import the certificate from this new keystore into the keystore used by your server <o:p> </o:p>
In ikeyman open the ibm-team-ssl.p12 keystore (or whatever your elm liberty server is using) look for it in JazzTeamServer702\server\liberty\servers\clm\resources\security <o:p> </o:p>
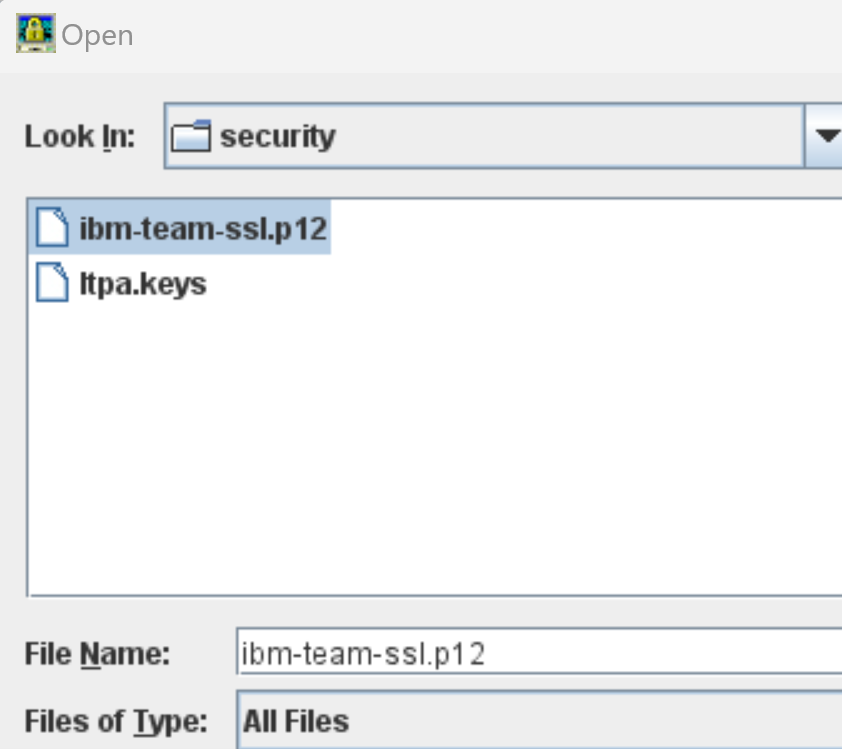
Import your new certificate from your new keystore into this keystore in order for the server to accept logins from this user. <o:p> </o:p>
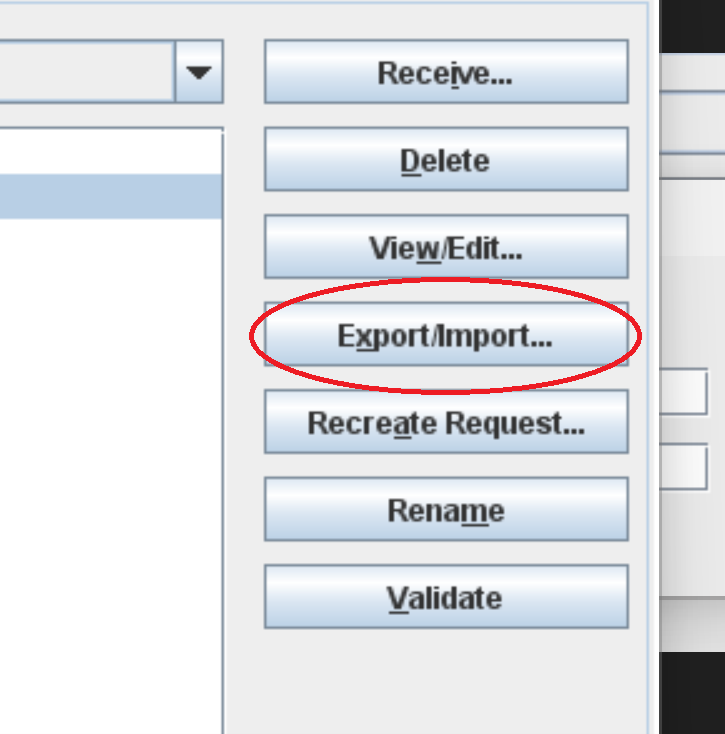
Your keystore should end up looking like this: <o:p> </o:p>
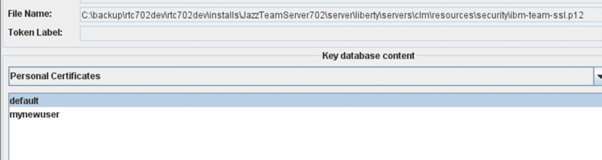
Finally copy the mynewuser.p12 keystore to the server running your builduser <o:p> </o:p>
Update apps to failover to certificates <o:p> </o:p>
Stop the liberty server and update the web.xml of each of the apps using security - (like JTS and CCM) <o:p> </o:p>
You need to update them in both JazzTeamServer702\server\liberty\servers\clm\apps and the template in JazzTeamServer702\server\liberty\clmServerTemplate\apps <o:p> </o:p>
Edit JazzTeamServer702\server\liberty\servers\clm\apps\ccm.war\WEB-INF\web.xml <o:p> </o:p>
(we are using Kerberos in our case with failover to certificate so no form) <o:p> </o:p>
<!-- <o:p> </o:p>
<login-config> <o:p> </o:p>
<auth-method>BASIC</auth-method> <o:p> </o:p>
<realm-name>Jazz</realm-name> <o:p> </o:p>
</login-config> <o:p> </o:p>
<login-config> <o:p> </o:p>
<auth-method>FORM</auth-method> <o:p> </o:p>
<form-login-config> <o:p> </o:p>
<form-login-page>/auth/authrequired</form-login-page> <o:p> </o:p>
<form-error-page>/auth/authfailed</form-error-page> <o:p> </o:p>
</form-login-config> <o:p> </o:p>
</login-config> <o:p> </o:p>
--> <o:p> </o:p>
<login-config> <o:p> </o:p>
<auth-method>CLIENT-CERT</auth-method> <o:p> </o:p>
</login-config> <o:p> </o:p>
Configure liberty to map certificates to users <o:p> </o:p>
Update the Liberty JazzTeamServer702\server\liberty\servers\clm\conf\ldapuserregistry.xml <o:p> </o:p>
In the <ldapRegistry tag add the following 2 lines: <o:p> </o:p>
certificateMapMode="CERTIFICATE_FILTER" <o:p> </o:p>
certificateFilter="uid=${SubjectCN}" <o:p> </o:p>
Finally edit the \JazzTeamServer702\server\liberty\servers\clm\server.xml <o:p> </o:p>
Add clientAuthenticationSupported="true" to the SSL tag <o:p> </o:p>
<ssl id="defaultSSLConfig" keyStoreRef="defaultKeyStore" sslProtocol="SSL" trustDefaultCerts="true" clientAuthenticationSupported="true" <o:p> </o:p>
enabledCiphers="TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA TLS_DHE_RSA_WITH_AES_128_CBC_SHA TLS_DHE_RSA_WITH_AES_128_CBC_SHA256"/> <o:p> </o:p>
Start the server again. <o:p> </o:p>