IBM Jazz + Eclipse Lyo = CSRF problem
Hello!
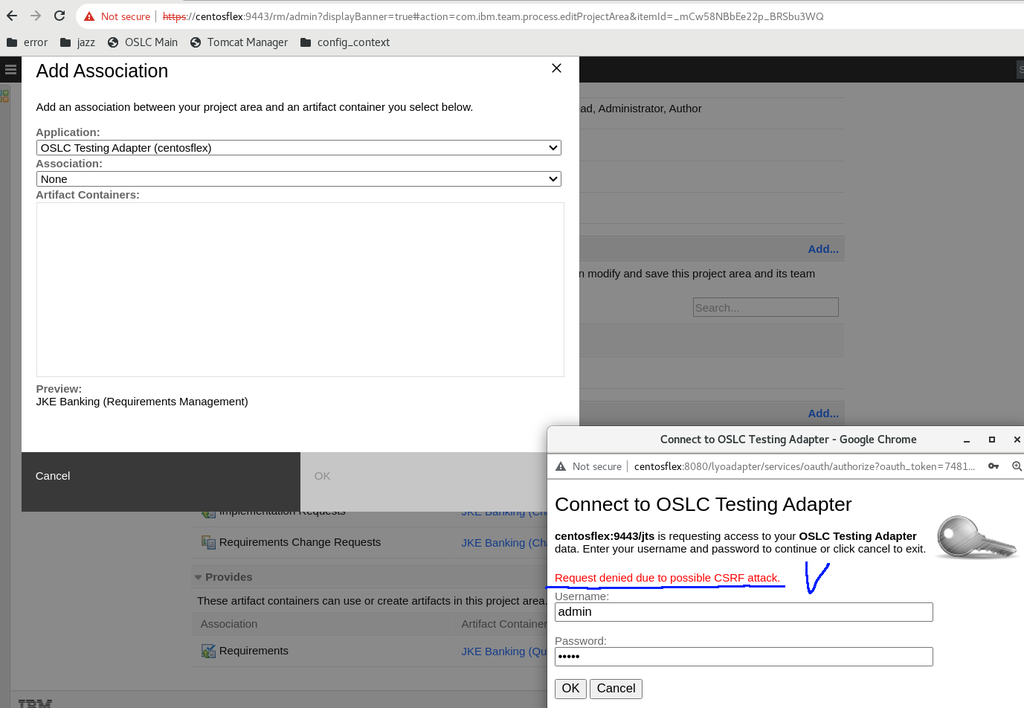
We want to develop an OSLC Adapter based on Eclipse Lyo v5.1.1.Final to integrate our custom testing solution with IBM Jazz RM v.7.0.2. We created a toolchain model, generated the code. Everything works well until we deploy the adapter on the same server where Jazz is installed. But we need to deploy OSLC Testing Adapter on an external server. For that, we changed baseURI from localhost to centosflex in our case. After we changed localhost to another name, we get CSRF attack problem.
Thank you!
Accepted answer
The most important information is missing - the call that causes this. Method? What did you send and what did you get. Headers you sent. One of my biggest struggles with Lyo has been that it is very hard to see the HTTP data it sends and receives. You need to use a proxy to trace the communication, I think.
Some hints.
- Always use a fully qualified host name. Never use localhost, except for the most basic testing. You can always add entries to the hosts file to fake full qualified host names on your localhost.
- As far as I can tell, Jazz Servers require the header X-Jazz-CSRF-Prevent with the JSESSIONID sent as value for POST requests.
- I would consider to setup your server with HTTPS from the very beginning as well. You eventually want to have this and the earlier you try it out and get the certificates done, the better.
Comments
Here one of the may results if you google CSRF site:jazz.net: https://jazz.net/forum/questions/98072/x-jazz-csrf-prevent-header-is-required-to-create-a-work-item-via-oslc-on-version-4001
Ralph, sorry! You are right! I was trying to describe the case in detail and forgot to point where I started at.
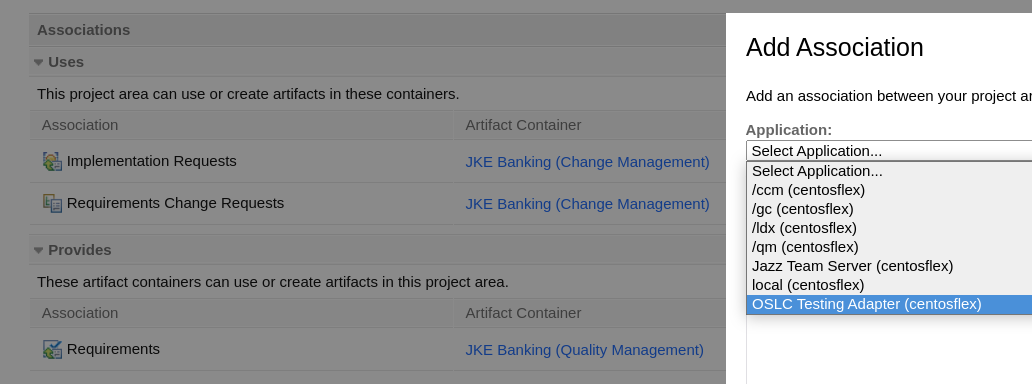
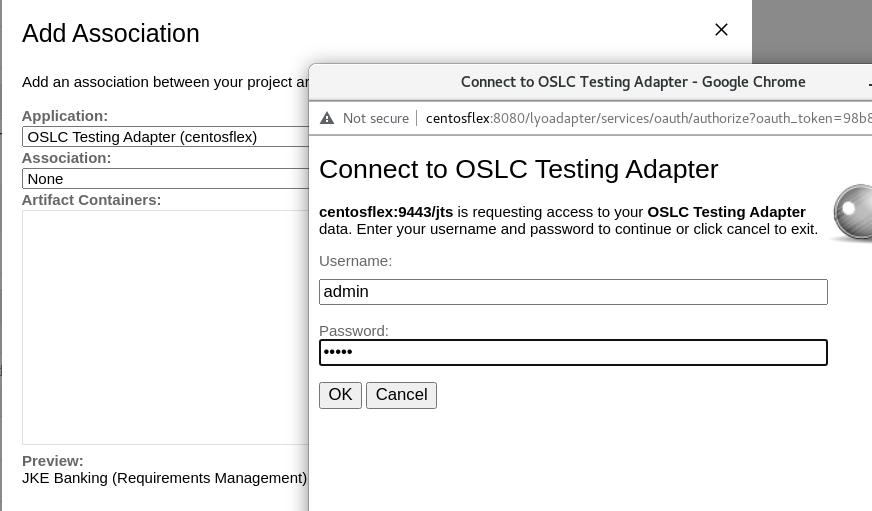
1. Register OSLC adapter in JTS as a friend (it was successful).
2. Go to project area (no GC context) and create an association.
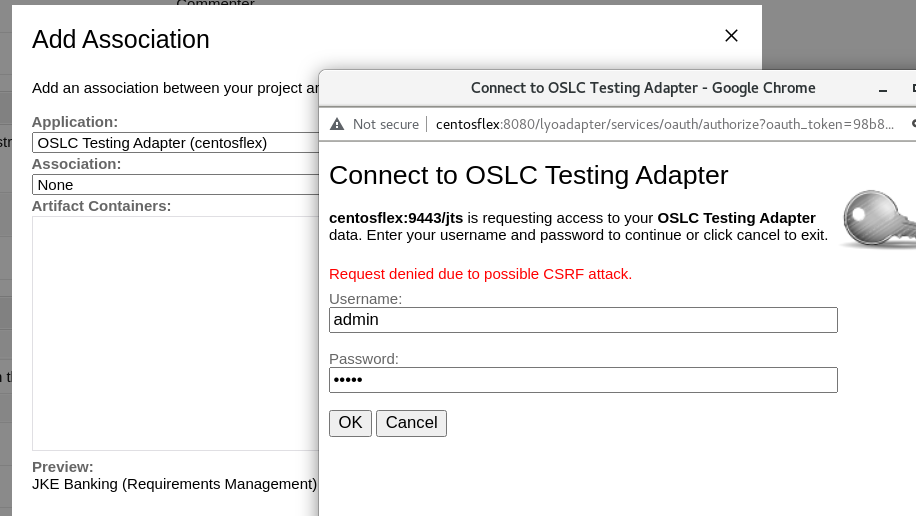
Thank you!
The question is: Is this request a POST? If you know which call it is, you should be able to tell. I had to send the X-Jazz-CSRF-Prevent in my Lyo code.
You can also ask in the Lyo project.
It seems that Jazz doesn't participate in this communication. Apparently, CSRF case is detected by Oath application delivered within Eclipse Lyo libraries.
This is the request analyzed in Chrome DevTools:
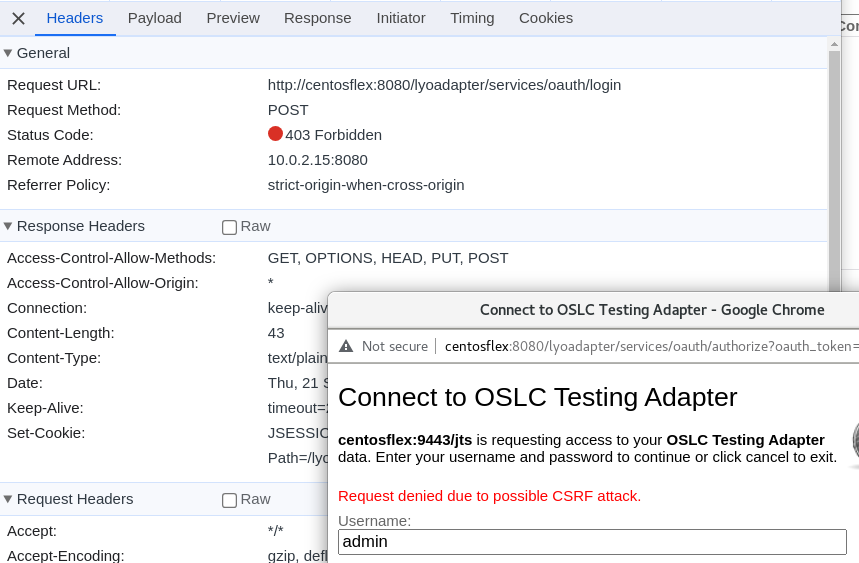
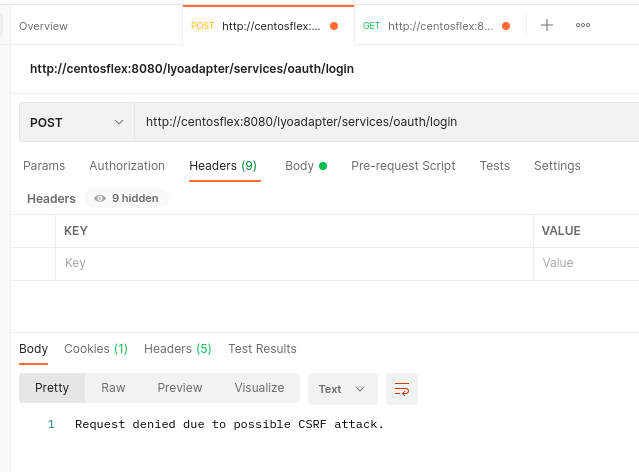
https://www.javatips.net/api/lyo.server-master/org.eclipse.lyo.server.oauth.webapp/src/main/java/org/eclipse/lyo/server/oauth/webapp/services/CSRFPrevent.java
If you use Lyo, you should be able to see the source code and be able to step through the authentication. You should also be able to see if you can add custom headers.
I would also suggest to ask here: https://forum.open-services.net/c/sdks/lyo/
You can also follow https://rsjazz.wordpress.com/2019/03/07/type-system-manager-part-2/ and find my code. Note that the code was created with an old version of lyo and the way I inject the header might no longer be available.
Thank you very much!
1 vote
Yes, a lot of problems gone out after testing the solution locally with HTTPS and a self-signed certificate. Thanks!
Yes, a lot of problems gone away after testing the solution locally with HTTPS and a self-signed certificate. Thanks!