Tip: Configuring Tomcat with LDAPLocalGroup Realm
Last Updated: June 4, 2010Author: Balaji Krish
Summary
The Jazz Team Server application runs in a secure application server. The application server manages the authentication and authorization. In order to do that, the application server retrieves the user information from an external user directory. LDAP is one of the external user registries supported by the Jazz application. To support authorization, the group membership of the users must be managed in the LDAP user registry. Some organizations do not have write access to the LDAP directory and thus cannot create group membership.
This document provides instructions on how to configure the Tomcat application server and the Jazz application to use the information present in the LDAP directory for authentication and a local file for managing authorization/group membership. This feature can be enabled by patching a RTC 2.0.0.2 IFix2 and RTC 2.0.0.2 IFix3 builds.
More Information
In order to support authentication using LDAP and authorization using the information in a local file, a new user registry type “LDAPLocalGroup” has been created. The following changes need to be made to authenticate using the user information present in the LDAP directory and authorize using the information present in the local group mapping file.
- Configure Tomcat to use the Jazz JNDI realm instead of the default JNDI realm. Change the realm to com.ibm.team.repository.localgroups.realm.LocalMappingJNDIRealm in conf/server.xml.
<Realm className="com.ibm.team.repository.localgroups.realm.LocalMappingJNDIRealm" debug="9" connectionURL="ldap://jazzxxx.torolab.ibm.com:389" userBase="ou=people,dc=jazz,dc=net" userSearch="(uid={0})" userSubtree="true" roleBase="ou=people,dc=xxx" roleSubtree="false" roleSearch="(memberNotAvailable={0})" roleName="cn" /> - Add the following in the GlobalNamingResources section of the conf/server.xml file. The globalNamingResources defines the global JNDI resources for the server. Set the pathname attribute to a mapping file (csv format) in the file system.
<!-- Local role mapping file that can be used by an authenticator to add roles to authenticated users --> <GlobalNamingResources ...> ... <Resource name="LocalRoleMap" auth="Container" type="com.ibm.team.repository.localgroups.IUserRoleMap" descripion="Role mapping file" factory="com.ibm.team.repository.localgroups.realm.RoleMappingResourceFactory" pathname="/opt/jazz/server/mapping.csv" /> ... </GlobalNamingResources>
Here is an example of mapping.csv. The mapping file will be used by Tomcat to determine the roles associated with the users.
In the example mapping file shown above, user balajik will have “JazzUsers” role while user srich has “JazzAdmins” and “JazzDWAdmins” roles.Sample Mapping.csv file balajik,JazzUsers
lavinm,JazzUsers
srich,[JazzAdmins; JazzDWAdmins]
schacher,JazzProjectAdmins
chaney,JazzUsers
sarcher,JazzGuests - Add the following entry to server/tomcat/conf/Catalina/localhost/jazz.xml to allow Jazz application to get access to the global JNDI resource.
<Context> <ResourceLink name="LocalRoleMap" global="LocalRoleMap" type="com.ibm.team.repository.localgroups.IUserRoleMap" /> ... </Context>
- The changes listed above allow the Tomcat application server to authenticate using LDAP directory and to authorize using the information present in mapping.csv file.
- [Optional] If the server supports LDAP synchronization, the registry type and settings must be changed in the Jazz application to import users, synchronize users and view the group membership of a user. These configuration properties can be changed in the ADMIN Web UI using Server->advanced properties page (e.g. https://localhost:9443/jazz/admin)
- Change the registry type to “LDAPLocalGroup” instead of “LDAP”
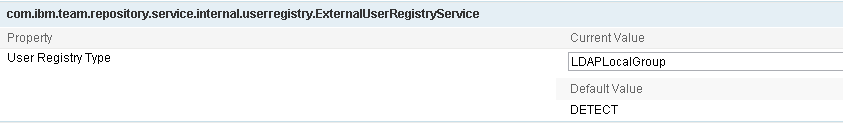
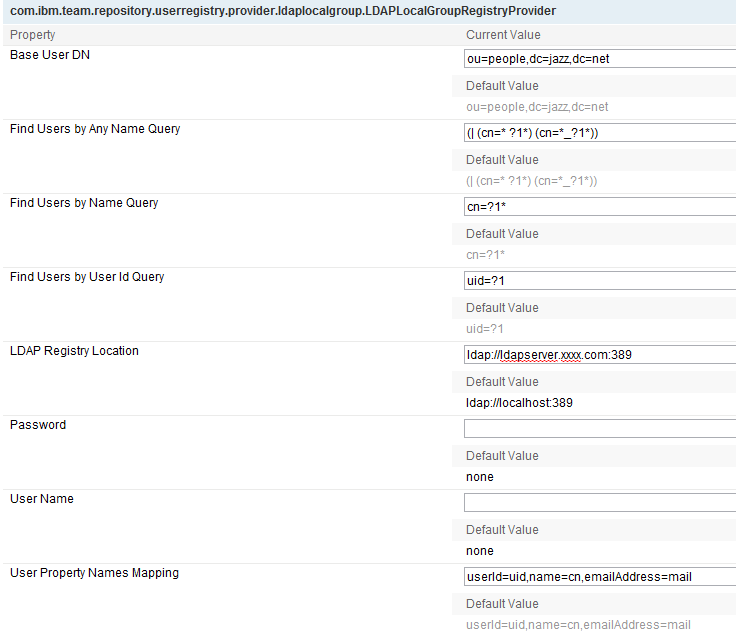
- Set the LDAPLocalgroup registry location, base user dn and user attribute mapping information. Note: These configuration properties are different from the ones for LDAP user registry provider.
How to install LDAPLocalGroup user registry in RTC 2.0.0.2IFix2 server and RTC 2.0.0.2IFix3?
LDAPLocalGroup user registry provider is not available in RTC 2.0.0.2 IFix 2. You need to patch the server to add support for LDAPLocalGroup.
- With a user id that has the JazzAdmins role, navigate to the following URL (change the server name if necessary):https://locahost:9443/jazz/admin/cmd/requestReset
- Stop the server.
- Update jazz/server/tomcat/conf/server.xml and jazz/server/tomcat/conf/Catalina/localhost/Jazz.xml according to the instructions mentioned above.
- Unzip the appropriate file for your installation:
- If you are using RTC 2.0.0.2 IFix2, unzip LDAPLocalGroup_patch_top_2002ifix2_20100520.zip in the directory where server.startup is located. Ensure the full path is preserved when unzipping.
- If you are using RTC 2.0.0.2 IFix3, unzip LDAPLocalGroup_patch_top_2002ifix3_20100520.zip in the directory where server.startup is located. Ensure the full path is preserved when unzipping.
- Verify the following new files exist
- tomcat/server/lib/localmapping-realm.jar
- update-site/features/com.ibm.team.repository.userregistry.localgroup.feature_1.0.2.201005201251.jar
- update-site/plugins/com.ibm.team.repository.localgroups_1.0.0.201005201209.jar
- update-site/plugins/com.ibm.team.repository.userregistry.provider.ldaplocalgroup_1.0.0.201005201209.jar
- conf/jazz/provision_profiles/ldaplocalgroup-profile.ini
- Add the following line in jazz/server/update-site/site.xml for the RTC server to pick up the new LDAPLocalGroup feature.
<feature url="features/com.ibm.team.repository.userregistry.localgroup.feature_1.0.2.201005201251.jar" patch="false" id="com.ibm.team.repository.userregistry.localgroup.feature" version="1.0.2.201005201251"> </feature>
- Restart the server
Related Information
The following links point to related information: