Tip: Configuring WAS with LDAP realm
Last Updated: October 31, 2008Author: Daniel Kogan
Summary
In this TechNote we will provide step by step guidance of how to setup WAS with LDAP realm to install Jazz Server including discussion on Application Server LDAP Configuration, LDAP filters and verifying LDAP connection.
For the General WAS setup with Jazz please follow this Installing Jazz Team Server with WAS article
More Information
Jazz uses J2EE container managed authentication for login and system permissions. In order for application security to work, you must configure a realm with the application server. While file based realm is generally OK for testing, the LDAP realm is recommended for production deployment.For more information on Authentication and Authorization please refer to this technote
For the WAS setup with file based realm please follow the Configuring WAS with Federated realm TechNote
LDAP Setup
In this section we will show how to setup and configure LDAP realm.
In order for Jazz to authorize a user authenticated by the application server, the user must be a valid Jazz repository contributor. Jazz is shipped with a bootstrap user called ADMIN pre-configured in the database. However, unless ADMIN / ADMIN is a valid set of credentials in the LDAP repository being used by WebSphere Application Server, you will not be able to login to Jazz after installing on WebSphere.
To avoid this issue, we will add at least one valid LDAP user as a Jazz repository contributor BEFORE configuring the security of Jazz on WebSphere Application Server using the Jazz setup WEB UI interface under User management tab.
Note
The pre-configured ADMIN user is pre-created in the Derby database. If you either use DB2, Oracle, your own instance of Derby or any other database, please make sure to run the “repotools” command to configure the data. For the instructions on how to run the “repotools” command please follow the instructions here.
LDAP Server Configuration
WebSphere Application Server LDAP configuration varies based on your particular LDAP server and schema. Before modifying your WebSphere LDAP configuration for Jazz, you should ensure that basic WebSphere LDAP functionality is functioning correctly. For complete information on configuring WebSphere Application Server for LDAP authentication, see the WebSphere Application Server InfoCenter article, Configuring Lightweight Directory Access Protocol user registries.
Retrieve the LDAP server SSL certificate (optional)
If your LDAP server is configured with Secure Socket Layer (SSL), you first need to retrieve the certificate from the server .
- Bring up the WAS admin console
- Expand Security and select SSL certificate and key management
- Click Manage endpoint security configurations
- Select the Outbound node for your appserver
- Click Key stores and certificates
- Click NodeDefaultTrustStore
- Click Signer certificates
- Click Retrieve from port button
- Fill in the following properties: Host, Port, Alias
- Click Retrieve signer information and hit OK
- Restart the server
WAS Setup
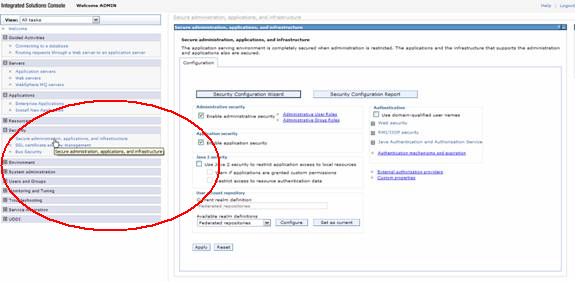
- In the WAS Admin Console go to Secure Administration, applications, and infrastructure menu option in the left menu column
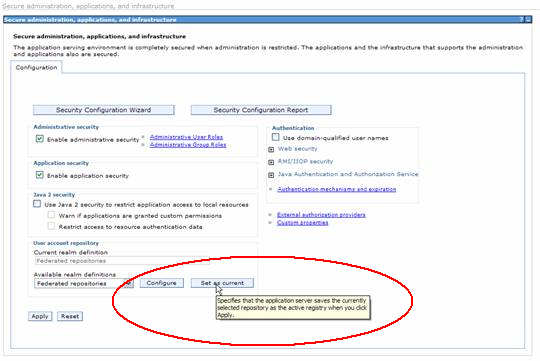
- For LDAP setup , choose Standalone LDAP registry. When selecting the Realm to configure Set as current button needs to be activated in order to save this option.
- Press the Configure button to go into Realm Configuration Screen.
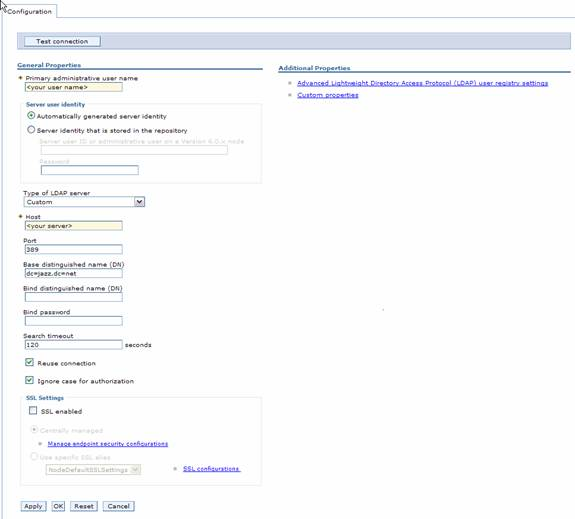
- Primary Administrative user name is set to the valid LDAP user
- Host is the correct LDAP host
- Port is the LDAP anonymous connection port. If SSL is enabled, the default port is 636, if SSL is not enabled, the default port is 389.
- Base Distinguished Name (DN) is base user DN in the LDAP directory
- Select SSL enabled if the server requires SSL connection
- Verify the LDAP server type (we used “Custom” for our testing)
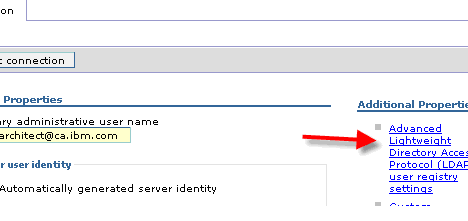
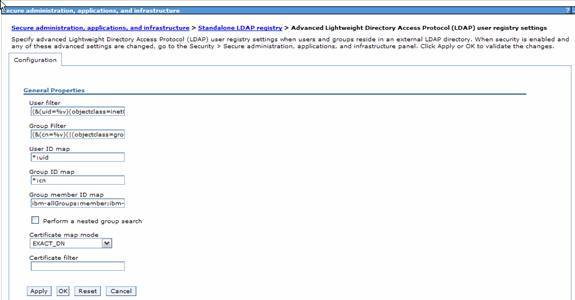
- Then click on Advanced Lightweight Directory Access Protocol (LDAP) user registry settings on the right.
- Specify the user and group filters.
- User Filter: (&(uid=%v)(objectclass=inetOrgPerson))
- Group Filter: (&(cn=%v)(|(objectclass=groupOfNames)(objectclass=posixGroup)))
- User id map: *:uid
- Group id map: *:cn
- Group member id map: ibm-allGroups:member;ibm-allGroups:uniqueMember
- These are just the example settings that assume that uid is used to represent the user id of a user in LDAP, cn is used to represent the name of a user in ldap
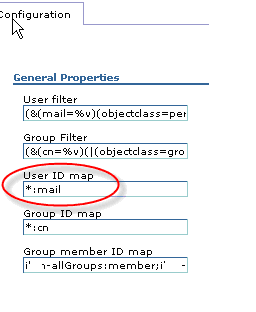
- For our purposes, the User ID map is important because this is the representation of the user that will be passed to Jazz. This attribute must match the userid that we created in the Jazz repository previously.
- The settings below are chosen based on our internal IBM LDAP server configuration. For more LDAP information please follow the LDAP Configuration TechNote
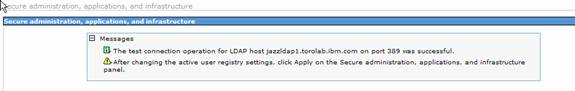
- Click the Test connection button to verify the settings
- If all the settings are correct, you will see this message
- Click Apply, then Save the master configuration and restart the WAS process.


Assigning User Roles
In this section we will show how to assign roles and permissions to the users loaded from LDAP server.
It is an important step in the LDAP deployment to setup users from LDAP with proper permissions in WAS before application deployment.
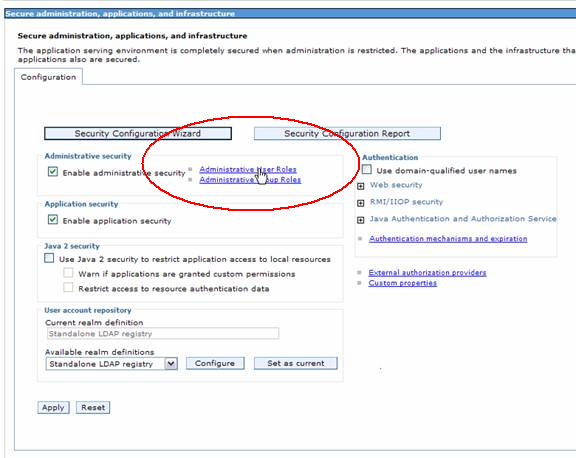
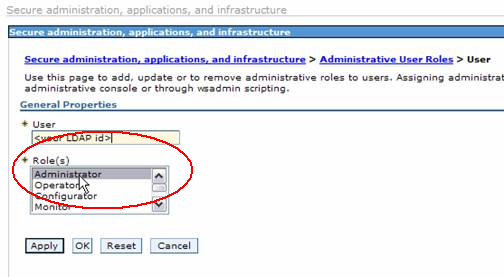
- In order to do so click on Administrative User Roles button from Secure administration, application, and infrastructure screen.
- On the User Roles screen use Add button to query for users from LDAP
- Grant the user appropriate permissions.
- The click on Apply and Save.

Assigning Group Roles
In this section we will show how to assign roles and permissions to the groups loaded from LDAP server.
Note
This step is optional, however it verifies that the group filter is setup properly and the Jazz application will be deployed and started without any Group permissions related problems.
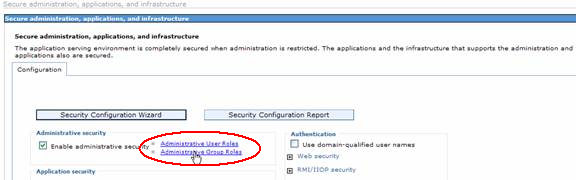
- Click on Administrative User Roles from Secure administration, application, and infrastructure screen
- On the Group Roles screen use Add button to query for groups from LDAP Make sure that you choose the existing user group from LDAP and successfully assign a role to it.
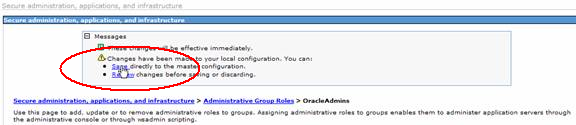
- In case of success, you should see this message.
- Click on Save to save the settings.

Logging back to WAS after LDAP Configuration setup
Once you completed LDAP Realm setup and restarted the WAS server, you have to login into WAS admin console using valid LDAP user/password.
- Open the admin console, you should be prompted for a userid/password
- Enter your userid/password
- You can verify the value returned by the User Id map by looking at the Welcome message at the top of the WebSphere Application Server Administrative Console.

If this value does not match the userid you entered in the Jazz repository, you will either need to add a corresponding userid in the Jazz repository or modify the User ID map property in the
WebSphere Application Server Administrative Console to return an appropriate value.
References
Links and related topics: