r15 - 2023-04-06 - 08:04:05 - ShubjitNaikYou are here: TWiki >  Deployment Web > DeploymentInstallingUpgradingAndMigrating > JazzAuthorizationServer > JASSCIMFederatedRepositories
Deployment Web > DeploymentInstallingUpgradingAndMigrating > JazzAuthorizationServer > JASSCIMFederatedRepositories
Multiple User Registries with Jazz Authorization Server and SCIM 
Author: ShubjitNaik Build basis: JAS and CLM Version 6.0.6.1 and higher
WebSphere Application Server Liberty Profile allows configuring Multiple federated registries. User registry federation is used when user and group information is spread across multiple registries. For example, the information might be in two different LDAPs, in two subtrees of the same LDAP, in a file, or the users are of a system. The information might even be in a custom user data repository. With registries federated, you can search and use these distributed user information in a unified manner with continuous store of information. Using federated registry, you can use the unified view for authentication and authorization of users in Liberty.
Jazz Authorization Server (JAS) is based on WebSphere Liberty Profile and can leverage the feature of configuring federated Registries. However, for it work with CLM, you would have to configure JAS with SCIM. This article focuses on steps to configuring JAS for SCIM and with federated registries.
Jazz Authorization Server (JAS) is based on WebSphere Liberty Profile and can leverage the feature of configuring federated Registries. However, for it work with CLM, you would have to configure JAS with SCIM. This article focuses on steps to configuring JAS for SCIM and with federated registries.
Important Notes and Pre-requisites
- To configure Multiple Users Registries with JAS, enabling SCIM configuration is Mandatory
- It is recommended to upgrade to CLM and JAS Version 6.0.6.1 (latest iFix) or higher to configure SCIM with JAS
- To configure SCIM you must use Lightweight Directory Access Protocol (LDAP) for User registries
- The screenshots on the SCIM configurations in CLM / ELM are from version 6.0.6.1
Setup and Configure JAS for SCIM with a Single LDAP Registry
- To configure SCIM you must use Lightweight Directory Access Protocol (LDAP)
- The first step is to configure JAS for SCIM with a Single LDAP Registry and complete JTS setup with JAS and SCIM
- Refer article Configuring Jazz Authorization Server for SCIM for the complete steps
Configure JAS for SCIM with Multiple LDAP Registries
Enable federated registries features in Liberty
- Enable the Jazz Authorization Server to support Federated Registries
- Edit
JazzAuthServer_install_dir/wlp/usr/servers/jazzop/server.xmland include the following in the list of features -
<feature>scim-1.0</feature> <feature>appSecurity-2.0</feature> <feature>servlet-3.0</feature> <feature>ldapRegistry-3.0</feature>
Modify LDAP configuration to include multiple registries
- We have included a few examples from different federated LDAP environments (MS Active Directory and ApacheDS) to help guide the configuration
- Edit
JazzAuthServer_install_dir/wlp/usr/servers/jazzop/ldapUserRegistry.xmland modify to match your environment, examples below
Microsoft Active Directory
-
<server> <ldapRegistry ldapType="Microsoft Active Directory" baseDN="CN=Users,DC=HOST1,DC=com" bindDN="CN=CLM Admin,CN=Users,DC=HOST1,DC=com" bindPassword="********" host="ldapserver1" id="ldapserver1:389" ignoreCase="true" port="389" realm="ldapserver1:389" recursiveSearch="true" sslEnabled="false"> <activedFilters userFilter="(&(sAMAccountName=%v)(objectcategory=user))" groupFilter="(&(cn=%v)(objectcategory=group))" userIdMap="user:sAMAccountName" groupIdMap="*:cn" groupMemberIdMap="memberOf:member" > </activedFilters> <attributeConfiguration> <attribute name="cn" propertyName="displayName" entityType="PersonAccount"/> <!-- propertyName is the scim property, name is the ldap property--> </attributeConfiguration> </ldapRegistry> <ldapRegistry ldapType="Microsoft Active Directory" baseDN="CN=Users,DC=HOST2,DC=com" bindDN="CN=CLM Admin,CN=Users,DC=HOST2,DC=com" bindPassword="********" host="ldapserver2" id="ldapserver2:389" ignoreCase="true" port="389" realm="ldapserver2:389" recursiveSearch="true" sslEnabled="false"> <activedFilters userFilter="(&(sAMAccountName=%v)(objectcategory=user))" groupFilter="(&(cn=%v)(objectcategory=group))" userIdMap="user:sAMAccountName" groupIdMap="*:cn" groupMemberIdMap="memberOf:member" > </activedFilters> <attributeConfiguration> <attribute name="cn" propertyName="displayName" entityType="PersonAccount"/> <!-- propertyName is the scim property, name is the ldap property--> </attributeConfiguration> </ldapRegistry> <federatedRepository> <primaryRealm name="FVTRegistry"> <participatingBaseEntry name="CN=Users,DC=HOST1,DC=com"/> <participatingBaseEntry name="CN=Users,DC=HOST2,DC=com"/> </primaryRealm> </federatedRepository> <administrator-role> <user>adadmin</user> <user>ad2admin</user> </administrator-role> </server>
- Users or Groups listed under
<administrator-role>tag are SCIM Administrators - The configuration under
< attributeConfiguration >is mandatory for each LDAP server configuration as thedisplayNameSCIM property is mapped to Name attribute in CLM / ELM. You can change the LDAP attribute mapping fromcnto as per your organization's requirement.
ApacheDS
-
<server> <ldapRegistry ldapType="Custom" baseDN="dc=clm,dc=com" host="ldapserver1" id="ldapserver1:10389" ignoreCase="true" port="10389" realm="ldapserver1:10389" recursiveSearch="true" sslEnabled="false" timestampFormat="yyyyMMddHHmmss.SSSSSSZ"> <customFilters groupFilter="(&(cn=%v)(|(objectclass=groupOfUniqueNames)(objectclass=posixGroup)))" groupIdMap="*:cn" groupMemberIdMap="groupOfUniqueNames:uniquemember" userFilter="(&(uid=%v)(objectclass=inetOrgPerson))" userIdMap="*:uid" > </customFilters> <attributeConfiguration> <attribute name="cn" propertyName="displayName" entityType="PersonAccount"/> <!-- propertyName is the scim property, name is the ldap property--> </attributeConfiguration> </ldapRegistry> <ldapRegistry ldapType="Custom" baseDN="dc=example,dc=com" host="ldapserver2" id="ldapserver2:10389" ignoreCase="true" port="10389" realm="ldapserver2:10389" recursiveSearch="true" sslEnabled="false" timestampFormat="yyyyMMddHHmmss.SSSSSSZ"> <customFilters groupFilter="(&(cn=%v)(|(objectclass=groupOfUniqueNames)(objectclass=posixGroup)))" groupIdMap="*:cn" groupMemberIdMap="groupOfUniqueNames:uniquemember" userFilter="(&(uid=%v)(objectclass=inetOrgPerson))" userIdMap="*:uid" > </customFilters> <attributeConfiguration> <attribute name="cn" propertyName="displayName" entityType="PersonAccount"/> <!-- propertyName is the scim property, name is the ldap property--> </attributeConfiguration> </ldapRegistry> <administrator-role> <user>clmadmin1</user> <user>clmadmin2</user> </administrator-role> </server>
- The above example is from an ApacheDS server setup with Anonymous Authentication. Include the BindDN if necessary
- Users or Groups listed under
<administrator-role>tag are SCIM Administrators - The configuration under
< attributeConfiguration >is mandatory for each LDAP server configuration as thedisplayNameSCIM property is mapped to Name attribute in CLM / ELM. You can change the LDAP attribute mapping fromcnto as per your organization's requirement.
Update Administrators for Jazz Authorization Server
Map Groups or Users as JAS Administrators who can perform JAS CLI operations, register Applications to JAS and access WebSphere Liberty AdminConsole- To Map Groups and Users who would Administrate JAS
-
<oauth-roles> <authenticated> <special-subject type="ALL_AUTHENTICATED_USERS" /> </authenticated> <clientManager> <group name="MYJAZZADMINS" /> <user name = "MYSCIMADMIN" /> <group name="LDAP2_JAZZADMINS"/> <user name = "LDAP2_SCIMADMIN" /> </clientManager> </oauth-roles>
Test SCIM with multiple registries
- Now that JAS is configured with Federated Registries and SCIM, it is time to test if users from multiple registries are listed
- Start the server (Linux example)
$ cd JazzAuthServer_install_dir $ ./start-jazz - Access the SCIM API for Users with this URL and confirm Users from multiple registries are listed
https://fully_qualified_domain_name_of_JAS_server:defined_port/ibm/api/scim/Users - Access the SCIM API for Groups with this URL and confirm Groups from multiple registries are listed
https://fully_qualified_domain_name_of_JAS_server:defined_port/ibm/api/scim/Groups
JTS SCIM configuration to map to Multiple LDAP Registries
- It is assumed that JTS Setup was completed earlier and was configured with JAS for SCIM with instructions from Configuring Jazz Authorization Server for SCIM
- Login to JTS admin page as a JazzAdmin User from the First LDAP registry
- Click on Server > Advanced Properties and search for SCIM Configuration com.ibm.team.repository.service.jts.internal.userregistry.scim.SCIMUserRegistryProvider
- Edit Jazz Groups to Registry Group Mapping to include groups from Additional LDAPs
One Jazz group can be mapped to multiple groups. The user registry groups must be separated by a semi colon. For example, JazzAdmins=LDAPAdmins1;LDAPAdmins2 maps JazzAdmins group to LDAPAdmins1 and LDAPAdmins2
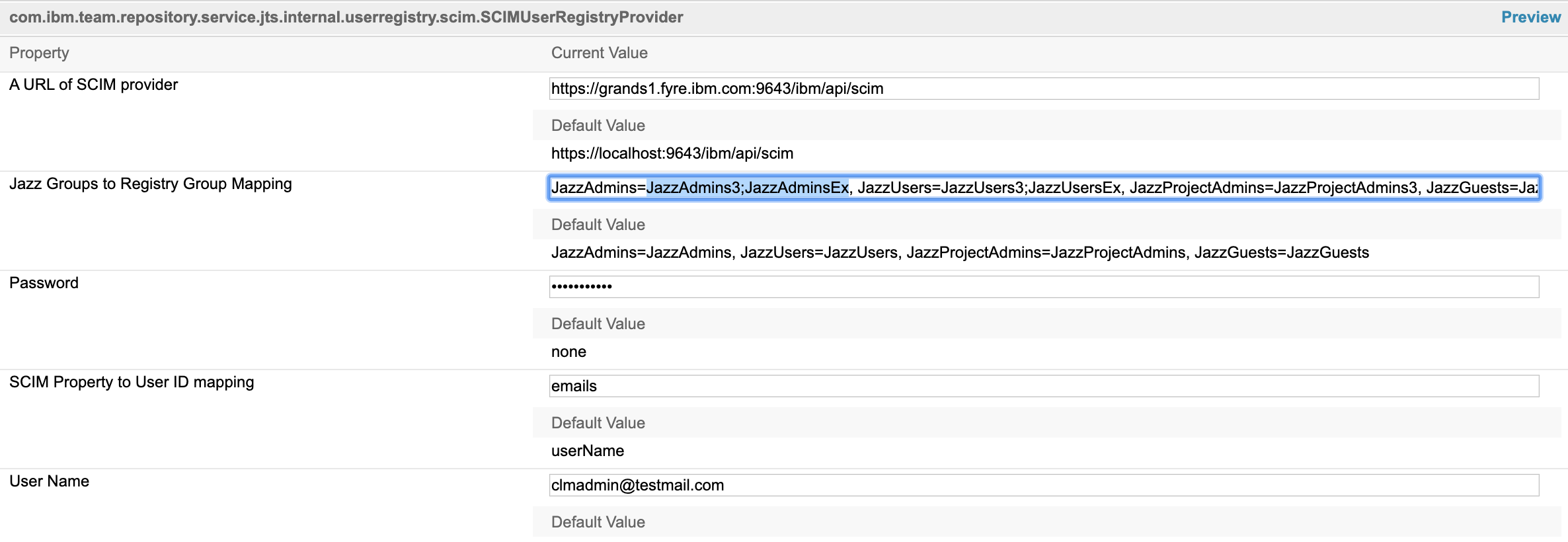
- Save the Configuration
- Confirm Users from different LDAP registries are able to Login with the Mapped Roles
Import Users
- By default User Synchronization operation picks UserID=sAMAccountName for Microsoft AD and UserId=uid for IBM Tivoli Directory Server and ApacheDS.
- If you wish to change the User ID mapping, follow the instructions from JAS and SCIM Article Configure SCIM Property To UserID Mapping
- Test by importing a user from each LDAP server manually
- Click on Users > Active Users > Import Users
- Enter a search term, click on the User and Import the user
- In the Active User Page, click on the newly imported user and confirm the UserId , Name and email maps to what you intended to configure
- If the verification is complete, you can then "Synchronize the users from multiple LDAP User registries to CLM
- Navigate to https:/jtsserver:port/jts/admin page > Home and Click on
Synchronize Jazz Team Server Users With External User Registry
- Navigate to https:/jtsserver:port/jts/admin page > Home and Click on
Related topics: Jazz Authorization Server, Configuring Jazz Authorization Server for SCIM
External links:
-
 Deployment web
Deployment web
-
 Planning and design
Planning and design
-
 Installing and upgrading
Installing and upgrading
-
 Migrating and evolving
Migrating and evolving
-
 Integrating
Integrating
-
 Administering
Administering
-
 Monitoring
Monitoring
-
 Troubleshooting
Troubleshooting
-
 To do
To do
-
 Under construction
Under construction
-
 New
New
-
 Updated
Updated
-
 Constant change
Constant change
- None - stable page
- Smaller versions of status icons for inline text:
-





Contributions are governed by our Terms of Use. Please read the following disclaimer.
Dashboards and work items are no longer publicly available, so some links may be invalid. We now provide similar information through other means. Learn more here.